
The state government of New York is using git! The github.com/nysenatecio site hosts GPLed tools launched by the New York State Senate, including open.nysenate.gov/openleg, which lets users search through ongoing legislative activities. The project seems very kernel-centric, even using a MAINTAINERS file similar to that of the Linux kernel. The data at the back end of these tools also is freely available, so people can write their own front-end sites or contribute to the state's effort. Neat!
The Xen developers are tasting the bitter pill of rejection. Many Xen users see a real need for Xen to be accepted into the kernel in the immediate future, but the kernel folks are holding out due to various problems. First, the Xen code is very invasive and apparently is not very respectful of the areas of the kernel it touches. As Linus Torvalds puts it, “Xen craps all over other people's code”, and elsewhere, he said, “Xen pollutes the architecture code in ways that no other subsystem does.” There also are certain features of Xen that people such as Alan Cox feel are badly implemented, to the point that they would create long-term maintenance and debugging problems for the kernel, which could not simply be backed out when better solutions arose.
The issues standing in the way of Xen inclusion in the Linux kernel, therefore, are all messy, difficult issues that would require the Xen Project in some ways to come to a screeching halt and move off in a different direction. The Xen developers currently are of a single voice in resisting this, but there's really no alternative. Their best bet probably is to submit small, sensible patches that make the kernel more and more naturally able to support Xen features. Alan Cox, Theodore Y. Ts'o, Ingo Molnar and others have expressed an interest in helping the Xen developers identify how best to direct their energies toward getting code into the kernel. But, just hoping that one day Linus decides Xen is too important to keep out of the kernel is traditionally a losing strategy.
Once a crucial driver and the topic of endless horrifying flame wars, the IDE code is changing hands yet again, from Bartlomiej Zolnierkiewicz to David S. Miller, who says he will consider IDE to be “legacy code”. IDE is, in fact, gradually being obsoleted by the PATA drivers, but there still are plenty of users tied to the IDE code, and so bug fixes and other enhancements will continue to be important for some time to come. The linux-next tree already has switched from using Bart's tree to David's, maintained at master.kernel.org:/pub/scm/linux/kernel/git/davem/ide-2.6.git.
Guo Hongruan announced that he'd successfully gotten Linux compiled and running on the TriMedia microprocessor, used typically for audio and video processing. TriMedia has no GCC target, making the port a difficult one. Guo had to run the kernel through a preprocessor to translate all the special GCC extensions into standard C99 source code, after which it compiled under the tmcc compiler. His work is available at tmlinux.googlecode.com.
Jon Masters has started a podcast of the linux-kernel mailing list, providing semi-daily summaries of events. He was inspired by the desire to force himself to keep up with the mailing list. Audio is available at kernelpodcast.org, and there's also an RSS feed available.
For quite some time, security experts have been claiming that Telnet is one of the worst protocols out there, and that it should be eradicated from the earth. According to these so-called experts, no one should use anything but SSH. Well, I'm here to show you that they are completely wrong. Telnet is one of the greatest gifts to humans.
The above paragraph should ensure some rabid e-mail messages. For those of you still reading, I actually am serious about Telnet. (Note: I am not talking about telnetd.) The Telnet protocol is made up of two parts: the server portion, telnetd, and the client portion, Telnet. Now, I won't pretend to disagree with the general attitudes toward the server portion, telnetd, and its inherent insecurities. But, I also think we shouldn't throw out the baby with the bathwater.
The client portion, Telnet, is a very useful tool in its own right. Say you're trying to configure your mail client and are running into problems. What options do you have? First, check to see whether the mail POP server is up. How? Why ping it, of course. Oh, but the IT staff drank the ICMP Kool-Aid and decided to block all ICMP traffic. So, now ping won't work. Are you stuck? Of course not—Telnet to the rescue.
How can you use Telnet in this situation? Telnet isn't limited to operating on the standard port. When you run Telnet, you can specify both a server and a port number. So, you can use it to try to connect to your mail POP server and check whether it's up by using:
telnet popserver.com 110
In this example, you're trying to connect to the POP server in order to read your mail. As Telnet operates over TCP, blocking ICMP packets shouldn't be troubling. Running the above, you should see a response like this (assuming that the mail server is up and running):
Trying X.X.X.X... Connected to popserver.com. Escape character is '^]'. +OK InterMail POP3 server ready.
Now you can see that the mail server is up, so there must be another issue. This is where Telnet becomes really useful. POP is a text-based protocol, like many other Internet protocols. Because it is just text going back and forth, you can use the Telnet client to talk to the mail server.
For the POP protocol, you simply can log in with your user name and password by using the following commands:
USER username PASS password -ERR invalid user name or password
With the above, you can check that you got the credentials right. As you can see in the example, the password is wrong. Trying again with the correct password gets you into the mail POP server. You can check whether you have mail with this command:
LIST +OK 0 messages
You even can use Telnet to send e-mail. If you have access to a mail server, you can connect to port 25 and send e-mail using the following:
telnet mailserver.com 25 Trying X.X.X.X... Connected to mailserver.com Escape character is '^]'. 220 mailserver.com ESMTP Postfix MAIL FROM:<user1@host1.com> 250 2.1.0 Ok RCPT TO:<user2@host2.com> 250 2.1.5 Ok DATA 354 End data with <CR><LF>.<CR><LF> From: user1@host1.com To: user2@host2.com Subject: Test Hello. This is a test of sending mail by telnet. Joey . 250 2.0.0 Ok: queued as 1DE8B2830E38 QUIT 221 2.0.0 Bye Connection closed by foreign host.
POP and SMTP are not the only text-based protocols on the Internet. You can use Telnet to check Web sites too. Most Web servers operate on port 80. If you want to check connection issues with a Web site, you can use this:
telnet google.com 80
And, you'll get a result like this:
Trying 74.125.45.100... Connected to google.com. Escape character is '^]'.
The HTTP protocol also is text-based, so if you want a particular page, use the following command:
GET index.html HTTP/0.9 200 OK Cache-Control: private, max-age=0 Date: Mon, 06 Jul 2009 18:29:40 GMT Expires: -1 Content-Type: text/html; charset=ISO-8859-1 Server: gws <!doctype html><html><head>.........
And, you will get the page back from the Web server. Telnet is the smallest and simplest mail client and Web browser, all wrapped into one. Of course, you need to have several Internet protocols memorized, but you really shouldn't be so lazy.
Using this ability, you also can do some basic system probing. With nmap, another popular tool, you can get a list of the open ports on a host machine. Starting there, you can try connecting to each of the ports and seeing what kind of output you receive. I had to do this recently with a remote site where I was having difficulty connecting to the host through SSH. Using Telnet, I was able to see the initial response from the SSH server as the following:
telnet host.com 22 Trying X.X.X.X... Connected to host.com. Escape character is '^]'. SSH-1.99-OpenSSH_3.9p1
This told me there was an issue with the particular version being run on the server, and I was able to go to the system administrator with an intelligent argument for upgrading the SSH server program.
It's still good to keep Telnet around—at least the client portion. Although the server portion has been considered a security risk in the past, the client portion can serve as a useful tool in network diagnostics. Sometimes old tools are the best, at least for some jobs. Have fun exploring your networks.
As the proud owner of both a Sony PRS-505 and a Kindle DX, it's quickly come to my attention that most eBook software is designed for operating systems other than Linux. With the Kindle, Amazon is trying to remedy that with computer-less converting over e-mail and such, but many of us want more local control. We also want to manage non-DRM books obtained from other vendors. Thankfully, the people behind the open-source Calibre fully support Linux with their Java-based program. Honestly, it's the best eBook management software available for any platform, so as Linux users, we're not sacrificing anything.
Calibre manages to do several things, and do them well:
It makes a sortable and searchable eBook library.
It converts eBooks to formats supported by all major eBook readers.
Books can be uploaded directly to the eBook readers.
It automatically retrieves metadata and cover art.
Blogs, newspapers and other on-line information can be downloaded automatically and converted to eBook formats.
With all those features, Calibre still manages to be free and open. If you own an eBook reader or are considering buying one, check out Calibre today: calibre.kovidgoyal.net.

Calibre in Action (screenshot from calibre.kovidgoyal.net)
ClamWin is an open-source antivirus program for Windows. ClamWin provides scheduled virus scans and automatic downloads of its regularly updated virus database. It also integrates with Explorer to provide right-click menu integration for scanning of individual files or directories. And if you're an Outlook user, it provides an add-in for removing infected attachments.
ClamWin is based on the open-source ClamAV engine, an antivirus toolkit for UNIX and UNIX-like systems (as well as Windows systems). ClamAV has built-in support for numerous types of archive files: tar, gzip, bzip2, zip, RAR, Cabinet, CHM and others. It also has built-in support for ELF and PE executables as well as compressed executables using numerous compression schemes. Many popular document formats also are supported: MS Office, Mac Office, HTML, RTF and PDF, among others.
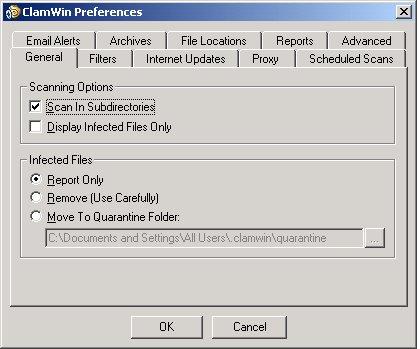
ClamWin Preference Pages (from www.clamwin.com)
There is a scene in the movie Lawnmower Man where every phone on the planet rings at the same time. Although Google may be the biggest technical force on the Internet, I don't think it's quite to that point. With the advent of Google Voice (www.google.com/voice), however, it's getting closer. The idea behind GV is that a single phone number can be used for all your telecommunications. Because I finally got an invite to the closed beta phase of Google Voice, I can explain a bit about it firsthand.
When (if?) you get an invite to Google Voice, it binds to your Gmail account. You get to pick a phone number from a giant pool of available numbers. The catch is you get to choose only one time. Many area codes are available, as are many exchanges within them. The coolest part about picking a number, however, is Google gives you a tool to alphanumerically choose. Think (123) Coke-Fan might be a nifty number? With the tool, you can test for availability. I like the number I got so much, I'm almost tempted to post it here—almost. Once you pick your number and verify at least one telephone, you get to set up rules. The rules are amazing.
Based on Caller ID, Google Voice will route calls however you desire (Figure 1). Contacts are placed into groups, and rules are set up for specific groups. It's possible for certain contacts to ring only certain phones, or you can have custom greetings for some people or even direct some people automatically to voice mail. In fact, with “call presentation”, you can listen in to voice mail while it's being left.
One issue with Google Voice is that if you call people directly with your cell phone (or home phone), they see your actual number instead of your Google Voice number. Thankfully, Google has a couple ways to solve that. If you look up the contact on-line, you can click a call button that calls both you and the person you are trying to reach. You answer your phone to hear it ringing on the other end. Another option is to call your own Google Voice number from one of your phones. You get a voice prompt to make a call, and then you type in the number for the person you are trying to reach. Not only is this a way to have others see your Google Voice number as the incoming call, but if you're lucky enough to have one of those cell-phone plans that allows for a certain number of “free” numbers, you can add your Google Voice number to your “circle” and never pay for minutes again (hopefully, there aren't any cell-phone companies reading this).
One more trick up the sleeve of the big Goog is what I refer to as its “Montana Magic”. If you get an SMS text message to your Google Voice number, it automagically is converted to a number in the (406) area code. Thankfully, the first few letters of the message display the contact name, because a random text message from an area code in Montana might be a bit hard to explain otherwise. Once that number is created, however, you can use it to call or text directly to your contact. The number will work only if it's called from one of your phones, but if you call it, the person on the other end sees your Google Voice number instead of your actual number. It is rather complicated, but brilliant as well.
Voice transcription, on the other hand, isn't exactly what I'd call brilliant. I'm absolutely certain it will get better with time. Why am I certain? Because it couldn't possibly get worse. I realize voice mail and voice-mail transcription are both free services, so I'm not really complaining, but the quality of transcription is indescribably horrible.
If you get a chance to get a Google Voice number, or if you were a GrandCentral (www.grandcentral.com) user that automatically was enrolled into the Google Voice beta pool, it really is a fun service to play with. I must admit, I'm a bit leery about publishing the number as my single point of contact, because since Google Voice is a free service, it could vanish at any time. The thought of business cards and such being worthless in an instant is a bit disheartening. As a way to shield your cell-phone number and add some phone-spam protection, however, Google Voice is quite a nice tool.
1. Number of Google groups with more than 100,000 members: 33
2. Number of Google groups that receive more than 10,000 messages per month: 28
3. Number of Google groups that receive 0 messages per month: 4,331,894
4. Number of Google groups related to computers: 92,681
5. Number of Google groups related to computers that receive 0 messages per month: 74,307
6. Percent of global Internet users that visit google.com (Alexa site rank #1): 32
7. Percent of global Internet users that visit yahoo.com (Alexa site rank #2): 26
8. Percent of global Internet users that visit youtube.com (Alexa site rank #3): 19
9. Percent of global Internet users that visit facebook.com (Alexa site rank #4): 19
10. Percent of global Internet users that visit live.com (Alexa site rank #5): 16
11. Number of articles in Linux Journal's article database: 9,116
12. Number of times the word Linux appears in LJ's article database: 37,671
13. Number of times the word Windows appears in LJ's article database: 4,956
14. Number of times the word kernel appears in LJ's article database: 7,796
15. Number of times the word KDE appears in LJ's article database: 1,367
16. Number of times the word GNOME appears in LJ's article database: 1,169
17. Number of hits per month on linuxjournal.com from the Yahoo Web crawler: 335,310
18. Number of hits per month on linuxjournal.com from the Google Web crawler: 310,270
19. US National Debt as of 07/05/09, 15:30:12pm MST: $11,501,541,973,785.60
20. Change in the debt since last month's column: $97,726,931,237.70
1–5: Google
6–10: www.alexa.com
11: MySQL
12–16: fmt -1 | sort | uniq
17, 18: Drupal
19: www.brillig.com/debt_clock
20: Math
I want all my code to be open source, but I will use the best tool for the job, and BitKeeper was the best tool, and at the time the alternatives sucked so bad. When the alternatives are so bad, I will take proprietary code. Proprietary was a downside, but what choice did I have? Hey, I usually do my presentation slides in PowerPoint.
—Linus Torvalds
Looking at the proliferation of personal Web pages on the Net, it looks like very soon everyone on Earth will have 15 megabytes of fame.
—M.G. Sriram
Information on the Internet is subject to the same rules and regulations as conversation at a bar.
—George Lundberg
Any sufficiently advanced bug is indistinguishable from a feature.
—Rich Kulawiec
A people that values its privileges above its principles soon loses both.
—Dwight D. Eisenhower
It's always the good men who do the most harm in the world.
—Henry Adams
If you're a Linux Journal reader, chances are you're pretty familiar with the command line. Don't let that stop you from heading over to our Web site and checking out our daily tech tip videos. Heck, I make the majority of them, and I still learn stuff from time to time. Even if you know every tip we throw at you, feel free to deflect new users at us. I must warn you, however, before you know it, those “n00bs” will end up knowing more tips and tricks than you. Don't say we didn't warn you!
A little hack here and a little tweak there, and you have a new LinuxJournal.com.
While working on the new version of the site you all know and love, I have thought about the word “hack” a lot. I think we in the Open Source community in particular have found “hack” to be a useful term with a broad definition. When working with software and platforms that are community supported, there is not always a “right” way to do things or a well-documented process. Thus, we find ourselves making our own recipes and hacks to get the job done whichever way we can. To me, a new way of laying out a Web page may require a workaround that I think of as a theming hack, or I may need to write or modify a Drupal module in order to add functionality to avoid hacking, as I always follow the first rule of Drupal, “don't hack core!” Are these code modifications worthy of the word “hack”? I can't break in to a secure network, but I can (usually) find a solution to a Web development conundrum.
Maybe we're all hackers then. As you read through this month's articles focused on hacks, I hope you discover a new way of solving your problems, a workaround that saves you some time, or even just a bit of inspiration that leads you to something new and different. Then, visit LinuxJournal.com to share your hacks with the rest of us!