Insecurity News |
| MySQL |
|
MySQL is a multi-user, multi-threaded SQL database server. A number of security issues that affect the mysql-server package have been reported. Oleksandr Byelkin discovered that "ALTER TABLE ... RENAME" checked the CREATE/INSERT rights of the old table instead of the new one. The Common Vulnerabilities and Exposures project has assigned the name CAN-2004-0835 to this issue. Lukasz Wojtow discovered a buffer overrun in the mysql_real_connect function. In order to exploit this issue an attacker would need to force the use of a malicious DNS server (CAN-2004-0836). Dean Ellis discovered that multiple threads ALTERing the same (or different) MERGE tables to change the UNION could cause the server to crash or stall (CAN-2004-0837). Sergei Golubchik discovered that if a user is granted privileges to a database with a name containing an underscore ("_"), the user also gains the ability to grant privileges to other databases with similar names (CAN-2004-0957). A number of small bugs related to the MySQL database system, including some potential security problems associated with careless handling of temporary files, were also discovered. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the names CAN-2004-0381, CAN-2004-0388, and CAN-2004-0457 to these MySQL security issues. Gentoo reference: GLSA 200410-22 / MySQL Mandrake reference: MDKSA-2004:119 Red Hat reference: RHSA-2004:569-16 |
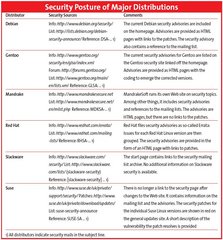
| Security Posture of Major Distributions |
|

|
| IPtables |
|
Faheem Mitha noticed that the iptables command, an administration tool for IPv4 packet filtering and NAT, did not always load the required modules on its own as it was supposed to. This could lead to firewall rules not being loaded on system startup. This caused a failure in connection with rules provided by lokkit at least. Users are advised to upgrade iptables packages. Debian reference: DSA-580-1 iptables Mandrake reference: MDKSA-2004:125 Suse reference: SUSE-SA:2004:037 |
| Apache |
|
The Apache HTTP server is one of the most popular web servers on the internet. mod_include is an Apache module to handle Server Side Includes (SSI). A possible buffer overflow exists in the get_tag() function of mod_include.c. If Server Side Includes (SSI) are enabled, a local attacker may be able to run arbitrary code with the rights of an httpd child process by making use of a specially-crafted document with malformed SSI. A heap-based buffer overflow has also been discovered in mod_proxy. mod_ssl was upgraded from version mod_ssl-2.8.19-1.3.31 to version 2.8.21-1.3.32 which corrects a flaw allowing a client to use a cipher which the server does not consider secure enough. A new PHP package (php-4.3.9) is also available for all of these platforms. More details about these issues may be found in the Common Vulnerabilities and Exposures database (CAN-2004-0492; CAN-2004-0885). Gentoo reference: GLSA 200411-03 / apache Mandrake reference: MDKSA-2004:122 Slackware reference: SSA:2004-305-01 |
| ImageMagick |
|
ImageMagick(TM) is an image display and manipulation tool for the X Window System. A heap overflow flaw has been discovered in the ImageMagick image handler. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the name CAN-2004-0827 to this issue. Red Hat reference: RHSA-2004:480-05 GLSA 200411-11 / imagemagick |
| libtiff |
|
libtiff is used by image viewers and web browsers to view "TIFF" images. Chris Evans found several-security related problems during an audit of the libtiff image handling library, some related to buffer overflows, some related to integer overflows and similar. This issue is being tracked by the CVE ID CAN-2004-0803. Matthias Claasen found a division by zero in libtiff. This is tracked by the CVE ID CAN-2004-0804. Further auditing by Dmitry Levin exposed several additional integer overflows. These are tracked by the CVE ID CAN-2004-0886. Additionally, iDEFENSE Security located a buffer overflow in the OJPEG (old JPEG) handling in the SUSE libtiff package. This was fixed by disabling the old JPEG support and is tracked by the CVE ID CAN-2004-0929. Mandrake reference: MDKSA-2004:109 Red Hat reference: RHSA-2004:577-16 Slackware reference: SSA:2004-305-02 Suse reference: SUSE-SA:2004:038 |
| Squid |
|
Squid is a full-featured Web proxy cache. iDEFENSE reported a flaw in the squid SNMP module. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the name CAN-2004-0918 to this issue. Debian reference: DSA-576-1 squid Gentoo reference: GLSA 200410-15 / squid Mandrake reference: MDKSA-2004:112 Red Hat reference: RHSA-2004:591-04 |
| Gaim |
|
The gaim application is a multi-protocol instant messaging client. A buffer overflow has been discovered in the MSN protocol handler. The CVE project (cve.mitre.org) has assigned the name CAN-2004-0891 to this issue. Updated gaim packages also fix multiple user interface, protocol, and error handling problems, including an ICQ communication encoding issue. Gentoo reference: GLSA 200410-23 / gaim Red Hat reference: RHSA-2004:604-05 Slackware reference: SSA:2004-239-01 |
| CUPS |
|
The Common UNIX Printing System (CUPS) is a print spooler. During a source code audit, Chris Evans discovered a number of integer overflow bugs that affect xpdf. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the name CAN-2004-0888 to this issue. When set up to print to a shared printer via Samba, CUPS would authenticate with that shared printer using a username and password. By default, the username and password used by CUPS to connect to the Samba share is written into the error log file. A local user who is able to read the error log file could collect these usernames and passwords. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the name CAN-2004-0923 to this issue. Debian reference: DSA-581-1 xpdf Mandrake reference: MDKSA-2004:116 Red Hat reference: RHSA-2004:543-15 Suse reference: SUSE-SA:2004:039 |