Insecurity News |
| CUPS |
|
The Common UNIX Printing System provides a portable printing layer for UNIX(R) operating systems. A buffer overflow flaw was found in the Decrypt::makeFileKey2 function of Xpdf which also affects the CUPS pdftops filter due to a shared codebase. An attacker who has the ability to send a malicious PDF file to a printer could possibly execute arbitrary code as the "lp" user. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the name CAN-2005-0064 to this issue. All users of CUPS should upgrade to these updated packages, which resolve these issues. DSA-645-1 cupsys GLSA 200501-30 / CUPS MDKSA-2005:018 RHSA-2005:049-08 SUSE-SR:2005:003 |
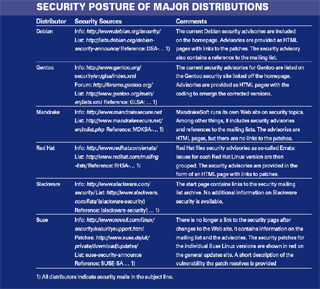
| Security Posture of Major Distributions |
|

|
| Linux Kernel |
|
The Linux kernel handles the basic functions of the operating system. This advisory includes fixes for several security issues: iSEC Security Research discovered a VMA handling flaw in the uselib(2) system call of the Linux kernel. A local user could make use of this flaw to gain elevated (root) privileges. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the name CAN-2004-1235 to this issue. A flaw was discovered where an executable could cause a VMA overlap, which could then lead to a system crash. A local user could trigger this flaw by creating a carefully crafted a.out binary on 32-bit systems, The flaw could also be triggered with a carefully crafted ELF binary on Itanium systems. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the name CAN-2005-0003 to this issue. iSEC Security Research discovered a flaw in the page fault handler code that could lead to local users gaining elevated (root) privileges on multiprocessor machines. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the name CAN-2005-0001 to this issue. A flaw in the system call filtering code in the audit subsystem allowed a local user to cause a crash when auditing was enabled. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the name CAN-2004-1237 to this issue. Olaf Kirch discovered that the recent security fixes for cmsg_len handling (CAN-2004-1016) broke 32-bit compatibility on 64-bit platforms such as AMD64 and Intel EM64T. A patch to correct this issue is included. A recent Internet Draft by Fernando Gont recommended that ICMP Source Quench messages be ignored by hosts. A patch to ignore these messages is included. MDKSA-2005:022 RHSA-2005:043-13 |
| Python |
|
Python is an interpreted, interactive, object-oriented, cross-platform programming language. Graham Dumpleton discovered that XML-RPC servers with the SimpleXMLRPCServer library that use the register_ instance() method to register an object without a _dispatch() method are vulnerable to a flaw allowing users to read or modify globals of the associated module. Remote attackers may be able to exploit the flaw in XML-RPC servers to execute arbitrary code on the server host with the rights of the XML-RPC server. Python users that don't make use of any SimpleXMLRPCServer-based XML-RPC servers, or making use of servers using only the register_function() method are not affected. Python users should upgrade to the latest version. GLSA 200502-09 / Python MDKSA-2005:017 |
| Squid |
|
Squid is a full-featured Web proxy cache designed to run on Unix systems. It supports proxying and caching of HTTP, FTP, and other protocols, as well as SSL support, cache hierarchies, transparent caching, access control lists and many other features. Squid contains several vulnerabilities: Buffer overflow when handling WCCP recvfrom() (CAN-2005-0211). Loose checking of HTTP headers (CAN-2005-0173 and CAN-2005-0174). Incorrect handling of LDAP login names with spaces (CAN-2005-0175). An attacker could exploit:
All Squid users should upgrade to the latest version. DSA-667-1 squid GLSA 200502-04 / squid SUSE-SR:2005:003 |
| Perl |
|
Perl is a high-level programming language commonly used for system administration utilities and Web programming. Kevin Finisterre discovered a stack based buffer overflow flaw in sperl, the Perl setuid wrapper. A local user could create a sperl executable script with a carefully created path name, overflowing the buffer and leading to root privilege escalation. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the name CAN-2005-0156 to this issue. Kevin Finisterre discovered a flaw in sperl that allows debugging information to be logged to arbitrary files. By setting an environment variable, a local user could cause sperl to create, as root, files with arbitrary filenames, or append the debugging information to existing files. The Common Vulnerabilities and Exposures project has assigned the name CAN-2005-0155 to this issue. The Debian Security Audit Project discovered that Perl's DBI library creates a temporary PID file in an insecure manner. A local user could overwrite or create files as a different user who happens to run an application using DBI::ProxyServer. The Common Vulnerabilities and Exposures project has assigned the name CAN-2005-0077 to this issue. MDKSA:2005:030 perl-DBI MDKSA:2005:031 perl RHSA-2005:069-08 RHSA-2005:105-11 |