The Sysadmin's Daily Grind: Smokeping
Smoked out!
By Charly Kühnast
The Sysadmin's Daily Grind: SmokepingSmoked out!By Charly Kühnast |

|
The Smokeping monitoring tool is on the package list of many distributions such as Debian and Gentoo. And if you can't find the package, the 200 KByte tarball from [1] is easy to install. Smokeping needs a few tools by the same author, such as RRDTool, Fping, SpeedyCGI, and a web server where it can display the results [2].
Smokeping uses a central configuration file that gives admins several useful examples. The configuration file is the place to configure the paths to the binaries and the web server. Things start to get interesting when you configure the alarm triggers, as Smokeping uses an extremely unusual but efffective format. One default trigger looks like this:
+bigloss type = loss pattern = ==0%,==0%,==0%,U ==0%,>0%,>0%,>0%
+bigloss is the trigger label. It has to be unique and alphanumeric. The type = loss entry pulls the trigger when packets go astray. The pattern entry gives the trigger a pattern to match. And the comma-separated entries are for the percentage of lost packets. By default, Smokeping pings the target twenty times every five minutes. If packets are lost in three consecutive pings, Smokeping pulls the trigger.
| SYSADMIN |
|
Admin Workshop: Backups | 66 Your data is never lost if you implement the right backup strategy. High Availability for VPNs | 68 Switch transparently to a backup tunnel without disturbing VPN connections. |
The second example is also taken from the default configuration:
+rttdetect type = rtt pattern = <10,<10,<10,<10,U <10,<100,>100,>100,>100
type = rtt means that Smokeping does not react to lost packets; instead it watches for notable increases in the round trip time. The comma-separated round trip values (in milliseconds) in the pattern line define a sequence. The example expects ping replies in less than 10 milliseconds. If a sequence of multiple RTTs of more than 100 milliseconds occurs (>100,>100,>100), Smokeping alerts you to the issue.
Okay so far, but Smokeping does not know which servers you want it to monitor. Another section lower down in the configuration file defines the target server. The default uses geographical sorting:
+World ++Europe +++UK +++Switzerland
I added my server:
menu = Germany title = Charlys Webserver host = kuehnast.com alerts = bigloss,rttdetect
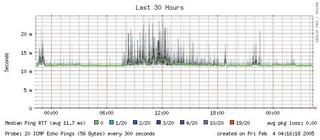
After launching Smokeping, the smokeping.cgi tool, which is part of the package, displays the server reply times (see Figure 1). If one of these entries triggers notification, I am alerted by email. Smokeping can do a lot more than this, as the exhaustive documentation at [1] clearly shows. Now all I need is for my server to crash so I can see Smokeping in action.
| INFO |
|
[1] Smokeping: http://people.ee.ethz.ch/~oetiker/webtools/smokeping/ [2] Documentation: http://people.ee.ethz.ch/~oetiker/webtools/smokeping/docs/install.en.html |