
By Bruce Byfield
Security in GNU/Linux follows the principle of defense in depth. Instead of relying on a single method of ensuring security, GNU/Linux relies on a variety of techniques ranging from password authentication to firewalls and packet sniffers. However, one of the strongest security measures is also the simplest: permissions.
Permissions are attributes of a file that set what different categories of users can do with it - whether they read it, modify it, or view it at all. In other words, permissions help users ensure both the safety of their work and their privacy on a multi-user system. In the worst case scenario, permissions can help safeguard other user's files when a cracker gains access to one account on the system.
However, as you often hear, everything in a GNU/Linux operating system is treated as a file. Even peripheral hardware is handled as though it were a file. Consequently, because every file has its own permissions, you can control who can use a piece of hardware by changing permissions on the appropriate file. For instance, in many distributions, to use a scanner, you need a user account that belongs to a group called scanner. Similarly, on older or high-security systems, you might need to be root user to mount a DVD or a USB drive.
Of course, many people pay little attention to permissions. Yet, as these examples show, permissions can matter, regardless of whether you are the sole user of a home system or one of thousands of users on a server. Although the encoding of permissions can be cryptic, learning how to read them and how to set them can be an important step in gaining control over your computing.
Permissions are assigned for three categories of users: the user account in which the file was created or downloaded, other members of the group to which the user belongs, and other users on the system. On most desktop systems, a new or downloaded file is automatically assigned to a unique group with the same name as the user account, which, practically speaking, reduces the categories to two. However, on networks, the group might consist of collaborators on a specific project, members of the same department, or any other collection of people who might need limited access to the file.
For each of these categories, three main permissions exist: Read, write, and execute, which are usually presented in that order. The read permission determines whether a category of users can view the files at all, whereas the write permission determines whether a file can be edited or, in the case of a directory, whether files can be added or deleted from it. The execution permission applies primarily to binary files but, in the case of a directory, sets whether a category of users can move into it and make it the present working directory.
Additionally, files can also have special permissions. If the user permissions include Set UID on a binary file, then the process that the binary runs has the same rights as the file's user - a state that can be dangerous if the user happens to be root, and which is therefore best to use sparingly.
Set GID is similar, except that running the process gives the same privileges as the group to which the process belongs - or, in the case of a directory, generally means that any new files take on the same permissions as the directory's group, rather than the permissions belonging to the files' creator. Finally, a file can also be set as Sticky, which means that only the user or the root user can use it.
Any of these permissions can also be left unset. These days, UID, GID, and Sticky frequently are. If you are familiar with permissions only through a desktop, you should also be aware that the desktop names of permissions might differ from the command line.
For instance, in Gnome's Nautilus, permissions are None, Read-only, and Read and write for files, and List files only, Access files, and Create and delete files for directories (Figure 1). In the same way, KDE's Dolphin uses Forbidden, Can Read, and Can Read & Write for files and Forbidden, Can View Content, and Can View & Modify Content for directories (Figure 2, top).
These renderings of permissions can be confusing, but they are just different names for the same basic permissions. In Dolphin, at least, you can go to the Advanced Permissions dialog window to set permissions names to those used at the command line (Figure 2, bottom left).
Because spelling out permissions would be cumbersome at the command line, Unix-like operating systems such as GNU/Linux have two notation systems for summarizing them: symbolic or textural and absolute or octal.
In symbolic mode, permissions are written as a series of 10 characters. From left to right, the first character specifies whether the file is a file (-), directory (d), or link (l). The next three characters are for user permissions, the three after that for group permissions, and the last three for other users' permissions. In each group of three, the characters from left to right indicate read (r), write (w), and execute (x) permissions or are left blank (-). In addition, the execute field can be used to Set UID (s).
This notation is easy to read. For instance, if you see permissions written as drwxrw-r--, you know that:
Once you understand symbolic notation, reading it is much faster than explaining permissions in full.
Absolute mode is even more succinct, with the use of one character, where symbolic mode uses three. At its most basic, an absolute number consists of three digits - one each for the user, group, and others - written in base 8. To figure out what each digit should be, add up the values of each permission given: Read permission has a value of 4, write permission a value of 2, and execute a value of 1, and no permission is 0.
In other words, a value of 0 means that a user category has no permissions, and the file is invisible to those in that category. A value of 6 means that a category has read and write permission, whereas a value of 7 means that a category has all three permissions.
In practice, of course, a file would rarely have a value of 000, because that permission would mean that only the root user could even see it, much less edit or execute it. However, if you wanted strict permissions, you might use 700 so that only the user could use the file, or 722 so that the user had full permissions, and both the group and others could only view it.
Absolute notation is sometimes written with a fourth character at the start. If the character is 0, it is simply a placeholder. However, the fourth character can also set special permissions. A value of 4 or 2 indicates that UID or GID are in use, respectively, and a value of 1 says the file is Set Sticky.
Just like the other digits in absolute mode, those of the fourth character are cumulative, so a value of 5 would indicate that the special permissions UID and Set Sticky were both in use.
Once you understand what permissions are available and how to write them, you are ready to start using them. If you simply want to view the permissions on a file from the command line, enter ls -l. The result is a list of files with permissions in symbolic notation on the left (Figure 3). Surprisingly, given the usual thoroughness of commands, no easy way to display octal notations with the ls command exists, although I have seen scripts that perform this function [1].
By contrast, the chmod command edits permissions in both absolute and symbolic mode. Regardless of the mode you use, you might want to add the -v or --verbose option so that you can see the results of the command (Figure 4). Alternatively, you can use -c or --changes to see only the changes that are made by the command in both sets of notation. If you are working near the root directory and are nervous about crippling your system by changing the wrong permissions, you can also include the option --preserve-root - especially if you are using the -R or --recursive option to change the permissions on all the files and subfolders in a directory.
Regardless of what options you choose, using chmod in absolute mode is easy. In fact, I recommend it as the easiest way to using it. All you need to do is place the permissions in absolute mode after the command, followed by the files whose permissions you are editing. For example, chmod -R 1764 ./Downloads would
In comparison, symbolic mode is more complex with chmod, but it allows you to edit more precisely. The basic format for using symbolic mode with chmod is chmod [options] [edited category] [action setting] [permission setting] (Tables 1-3).
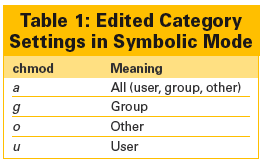
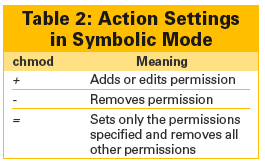
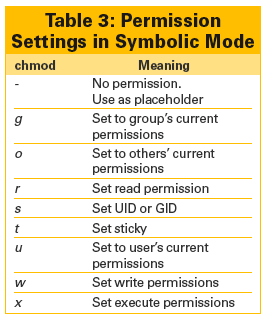
For instance, chmod -v a+rwx ./Pictures would edit permissions so that all categories of users had read, write, and execute permission on the directory /Pictures and all of its content. If you chose, you could use the category settings to edit just one category of user, the action setting to edit only one type of permission, or the permission setting either to specify the permission changed or to copy the existing permissions of one particular category of user for another.
The one difficulty is remembering all of these possibilities when you need them. Unless you are constantly using them, you could easily forget how to use them and have to look them up. The main advantage of using absolute mode with chmod is that it has fewer details to remember.
While you are editing permissions, especially when logged in as root, you might also want to change the owner and group for a file. When you do, you can use chown and chgrp. These two commands are similar in format, with the name of the new owner or group placed between the basic command and the files affected. For example, chown jason christmas.png gives the user jason ownership of the file christmas.png, whereas chgrp jason christmas.png changes the owner of christmas.png to jason.
If symbolic and absolute notation seem too much for you to retain, you have a point. Instead, you might prefer to choose a default set of permissions that are applied automatically. To do so, you need to alter the umask setting either by changing its value in /etc/profile or /etc/bashrc for all users or in ./bash_profile or ./.bashrc in the home directory for the current account. If you prefer, you can use the umask [setting] command, running it as root to change the setting for the entire system or as the current user to alter its default.
To view the current umask setting, use umask for octal mode or umask -S for modified symbolic mode (Figure 5).
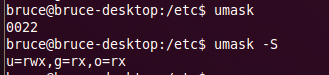
For reasons that are obscure to me, the umask value is an offset of absolute notation. In other words, if umask is set to 077, then you subtract 077 from the default octal mode of 666 for files and 777 for directories and, if necessary, round up to get default permissions of 600 for files (user can read and write; other categories of users cannot work with or view the file) and 700 for directories (user can read, write, and execute; other categories of users cannot work with the file)
Having set the umask value to a setting that offers the security you want, all your new files will use the new value without any more input from you. The exception is files from downloads or other users, so occasionally you might want to run the chmod command on your entire home directory so you have the security you prefer. Otherwise, once the umask value is set, you can mostly go about your business, confident that permissions form a reliable line of defense against intruders on both your system and your personal privacy.
| INFO |
|
[1] Show octal notation script: http://www.linuxforums.org/forum/linux-newbie/21722-command-shows-me-permissions-file-octal.html
|