
The newest kind of card for your pocketbook offers better security for the information it holds.
Credit card companies successfully marketed the silver card, the gold card and the platinum card. Precious metals represent wealth, and we were supposed to associate that notion with something less tangible—card security.
In today's society, better security for electronic commerce is a priority for corporations, banks and merchants. Even as computers become faster, methods of authentication once thought secure become easier to subvert. At the same time, modern communications allow hackers to advertise their exploits, making details of such activity easy to come by, even for amateurs. An easy-to-use exploit script is usually just a web site away. As current security methods become easier to crack and subvert, developers search for different and better ways of authentication.
We all use magnetic-stripe cards every day to get money from the bank, to shop, to fill the gas tank and to enter the office building. It's not uncommon for a person to carry ten or more different cards at any given time. Are the cards secure? Consider the following common credit card scenarios:
You pay your restaurant bill with a credit card and leave the receipt on the table.
You make a department store purchase with a credit card and later throw the receipt in the trash.
You send your mother flowers purchased over the Internet using a credit card number.
Card receipts contain all the necessary information for anyone to assume the same purchasing power (indeed, the same identity) as the actual card holder. In any of the above scenarios, it is only a matter of time before your identity and potentially your bank account is compromised. Authentication using magnetic-stripe tokens is plainly insecure.
Another example of weak authentication is the computer password—the most common method of authentication in computing today. Being the only person who knows a secret word or pass phrase gives us a misplaced sense of security about data access. We don't think about the adolescent cracking our password while we sleep, yet dictionary-based password crackers (software that tries common dictionary words) are available on the Internet. A software package such as Crack 5.0 easily reveals passwords in a matter of minutes—at most a few hours—that were once thought secure. Most hackers obtain initial access into a system through accounts with no password at all or a password set to match the user name. (Many system administrator packages set the default account name to match the user name, and the default never gets updated.)
You can strengthen current security mechanisms, but the ultimate solution may be an entirely new design. Soon magnetic-stripe credit cards, passwords and PINs could be things of the past, replaced by token-based authentication systems enabled with biometric sensors—a secure token storing cryptographic certificates and keys, and terminals with biometric sensors to qualify key access (e.g., from your fingerprint).
One such token is the smart card. Smart card technology has been reliably demonstrated in Europe for many years. A smart card is a special-purpose storage device about the size and thickness of a credit card, containing a thin microprocessor capable of storing data. When inserted into a suitable reader, the microprocessor is powered up, and instructions are passed between the host computer or terminal and the smart-card microprocessor.
Your wallet today: some cash, a few credit cards, an ATM card, a phone card, a driver's license, employee badge, a piece of paper with all your PIN numbers written on it and a reminder to buy milk.
Your wallet in the future: a single smart card with biometric authentication.
What can you do with that smart card? A single card has the potential to replace:
bank cards, ATM cards, phone cards, gasoline cards, credit cards in general
driver's license, passport, employment identification
physical access to your home, your car, your office
medical records and services
With biometrics, you might even be able to remember that you are allergic to dairy products or penicillin. Biometrics are measurements taken from a person to identify them later, such as fingerprints, retinal patterns, face photos, finger lengths, voice prints or typing and writing patterns. Measurements can be digitized for storage on a smart card and for use in conjunction with digital certificates and authentication.

Figure 1. Smart Card
Smart cards are true computing devices containing a CPU, ROM, EEPROM and RAM—all packed into a flexible plastic card. The technology of the microprocessor is comparable to that of a full-sized desktop computer in the late 1970s. Smart cards have an operating system, an I/O channel, static and dynamic memory and an instruction set used to program the card. In the future, the technology may evolve so that entire operating systems (such as Linux) could be run from the card. Right now, smart cards mainly provide secure, portable storage for cryptographic keys and a wide assortment of authentication information.
Smart cards, like ice cream, come in many different flavors, but there are two fundamental types: memory-only and processor-based.
Plain vanilla memory cards are typically used as electronic purses—for example, phone cards, vending machine cards or university campus cards that store cash value. The value can be decremented with each use and recharged at specialized machines; consequently, such cards are sometimes referred to as cash cards.
Processor cards enjoy a more varied deployment. They can contain a cryptographic coprocessor for authentication and file encryption. Some processor cards actually run Java binaries directly on the card using a built-in Java virtual machine (a subset of the one that runs on any full-sized computer) to interpret the commands in the Java binary. These are referred to as Java cards. Most of a Java card's functionality can be exercised through Java classes, allowing the card to be programmed in almost any platform or hardware specification. Java cards also include some limited cryptographic functionality, which can be accessed through Java security classes. Java cards combine the ease of a familiar programming language with the robustness of the smart card.
Both memory and processor smart cards support two types of I/O: actual electrical contacts or radio-frequency induction.
The burgeoning need for secure transactions and e-mail privacy may be answered by the next generation of cryptography cards, such as the Schlumberger CryptoFlex smart card. Such cards are capable of a wide variety of cryptographic functions, including random-number generation, digital signing and encryption. These cards are typically used in an authentication process, where cryptographic keys associated with an X.509 certificate are stored on the card and unlocked for use with a PIN number. Or biometric measurements on the card are compared with those retrieved through a card reader equipped with biometric sensors. After authentication, a user can access the public/private key pair directly on the card and use it to sign or encrypt messages using the card's cryptographic coprocessor. This key pair never leaves the card. The cards can store more than one key pair and are capable of doing multiple cryptographic algorithms such as PGP, RSA and DES.
Unlike the magnetic-stripe card, which uses single-factor authentication (you have the card in your hand, therefore it must be yours), cryptographic smart cards actually run software right on the card. This allows bi-directional authentication between the smart card and the card-reader terminal, and when biometrics are involved, multi-factor authentication. One possible authentication scenario runs like this:
The card reader terminal powers up the card and identifies it through the “Answer to Reset” function.
The reader initiates authentication by transmitting a random number to the card along with a request for encryption.
The card authenticates the user through a PIN or biometric measurement, and if successful, encrypts the random number using the private key stored on the card. The encrypted random number is returned to the reader along with the certificate of identity.
The card-reader terminal obtains the public key (using a directory lookup or other database) and decrypts the random number using the public key.
If the decrypted random number matches the one originally transmitted, the user and card are authenticated.
A similar process can even be used by the card to authenticate the reader terminal.
A card reader or terminal is required to power and communicate with the card. There are a wide variety of smart card readers on the market. They include contactless or RF readers, and the more common electrical-contact reader. These readers can be computers in their own right or can interface with any host computer via serial, parallel, USB and PCMCIA ports. Other reader-to-host interfaces are possible, even through a floppy drive. Some readers incorporate PIN pads or biometric sensors directly in the reader so that the PIN, pass phrase or biometric measurement never leaves the system.
Readers and terminals come in a variety of sizes, shapes, colors and functions. The Schlumberger Reflex 60 smart card reader is designed for PC applications—for example, secure business-to-business transactions between merchants and banks over the Internet. You could also have secure access to Web TV, games and many other applications.
Smart cards communicate with the reader through either the contact plates located on the plastic card or through radio frequency. In each case, the cards communicate through either the T=0 or T=1 protocol. T=0 is a byte-oriented protocol where an instruction byte is sent and an acknowledgment is received. This may be an error message or just an acknowledgment of the instruction. T=1 is a block-oriented protocol which sends a specified unit of data.
Like PCs, smart cards have a file system which contains a root or master file. All files are identified by two bytes. The master file on smart cards is identified by 3F 00. Dedicated files are similar to sub-directories in that they allow files to have specific paths. Information is actually stored in what is called the elementary file. The elementary file can be defined in different ways, depending on how the user wants it subdivided for storage. The following diagram shows a simple smart card file system.
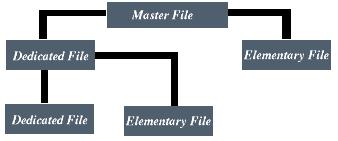
Figure 2. Smart Card File System
As smart cards work their way into our lives through cellular phones, stored-value and authentication systems, they will also make their way into our general computing environment. Linux provides a secure multi-tasking environment perfect for smart cards. Project MUSCLE (Movement for the Use of Smart Cards in a Linux Environment) is a virtual team of developers working to integrate smart cards, readers and security in an open fashion for the Linux environment. As the acronym implies, the MUSCLE team is trying to integrate all necessary smart-card hooks into the Linux world. See sidebar for contact information.

Figure 3. Muscle Logo
Several different MUSCLE projects are underway, such as an effort to integrate smart-card tokens with Pluggable Authentication Modules (PAM), interfaces for scripting languages such as Perl, and creating drivers and implementing APIs for different cards and readers. MUSCLE expects the following benefits from these activities:
Integrating smart cards into PAM will allow cross-platform authentication between an array of different operating systems.
Perl integration provides another environment for smart card use, in particular for those accustomed to the ease of string manipulation in Perl.
Standardizing card and reader APIs under Linux gives developers a common interface for integrating a wide variety of smart cards and readers with a wider variety of host computers.
Creating a Linux cryptographic API will handle cryptography for other PKCS-11 type devices as well as for smart cards.
Virtualization of the smart-card file system would allow a smart-card to be mounted as any other file system under Linux. This might allow the manipulation of the smart-card file system in an easy-to-use, familiar fashion.
Developing a means of using different biometric sensors with smart cards under Linux is another interest. Biometric fingerprint scanners such as American Biometric's hot new BioMouse and BioMouse Plus could easily make Linux the operating system of choice for high security applications such as banking.
MUSCLE posts all source code under the GPL on the web site http://www.linuxnet.com/smartcard/index.html, along with the author name, date and purpose. All code posted is covered under the GNU public license, allowing it to be freely distributed as long as the rules are followed. This is where open development occurs. For more information on the GNU public license, visit http://www.gnu.org/.
MUSCLE currently has support for the Schlumberger Reflex 62 and 64 card readers. These readers rely on the serial port for data communication and get their power from the keyboard or mouse port. The current drivers support all of the necessary functionality of the Reflex 62 and 64 readers, including PIN verification (Reflex 64 only). These drivers rely on the termios library for serial functionality and can be placed on any Com port. Currently, all Schlumberger CryptoFlex card functionality is supported, including ISO-7816 functionality and cryptographic functions (file reading and management, RSA signing, key and PIN verification, authentication, seek and other administrative functions).
Public interest in smart cards will spur technology growth and increase the need for a better user interface. An embedded operating system such as Linux can offer the ease of a UNIX-style operating system along with full functionality of the card. For example, to retrieve information about the file system directory structure, embedded Linux would allow a simple ls command to be used instead of the hex command 0xF0 0xA8 0x00 0x00 0x00. Currently, smart cards are not capable of an embedded operating system. Until they can, familiar shell commands such as ls could be accomplished on the smart card by virtualizing the shell—interpreting shell commands into their smart card hexadecimal counterparts. This would provide an easy way to personalize the card to fit customer needs.
What will customer needs be in the next millennium? Some people predict less emphasis on materialism. Exercise machines might be as prolific as ATMs, and the gold card may be less attractive than one with more brains. Securing the future always involves flexibility and change. Smart cards appear to combine it all.