
“Society is always taken by surprise at any new example of common sense.”
—Ralph Waldo Emerson
“You can never entirely stop being what you once were. That's why it's important to be the right person today, and not put it off till tomorrow.”
—Larry Wall
“I'm what you get when an eleven-year-old kid decides he wants to grow up to be a Heinlein character.”
—Eric S. Raymond
“FEATURE”
—VW Bug license plate spotted by ESR in California
“Kill processes, not people.”
—Larry Cohen
“You can make millions without exploiting. But not billions.”
—Alan Kay
“In battle, exploiting a situation deserves a medal. In business, exploiting a situation deserves condemnation.”
—Craig Burton
“Trust always breaks down first over money.”
—David Hodskins
“Web browsers are fragile assemblies of bugs, held together with Hello Kitty stickers. They tend to have problems with complicated pages, especially if they're long. Some of my pages are pretty long, and I want them to work with any web browser on any computer, and so I've been very careful not to do anything unkosher, daring, or cool.”
—James “Kibo” Parry
Last September, we ran a little piece called “Barrel Scrapings” that listed a couple dozen domain names that were still untaken. Since then, the domain name business has turned into an e-land rush. At the current rate, several new domains are claimed every second. That's a lot of “brands”, all bent on capturing your eyeballs, or whatever it is that e-marketers are after these days.
So we thought we'd step back into the fray to see just how insane this business has become.
First, we took a look at some of the names we suggested almost a year ago. “Earwig.com” is taken. So are “stoptalking.com”, “toygod.com” and “cashbird.com”. But “coaptathetic.com”, “bedkill.com”, “buttcramp.com”, “neithersex.com”, “petsurface.com” and “barfwash.com” are all still available. Hope lives.
In fact, hope abounds. Thanks to the good folks at Register.com, we found many domain names already taken, like “feces.com”, are blessedly unconfused by a host of derivative names. So Register.com kindly lists a pile of those names, each produced by adding an e-cliché prefix (e.g., “about”, “quick” and “cyber”) or suffix (e.g., “biz”, “search” and “dot”). So, if you're disappointed by missing your chance with “crap.com”, you can choose from any or all of the following:
aboutcrap.comcrapdot.comfreshcrap.comcrapmeat.comcrapforge.comcocrap.comcrapauction.comcrapexchange.comcrapbiz.comcrapbusiness.comcrapfirm.comcrapoffice.comcrapsearch.comeasycrap.comglobalcrap.cominteractivecrap.cominternationalcrap.comquickcrap.comsellcrap.comsmartcrap.comworkcrap.com
Sadly, mycrap, cybercrap, ecrap, quickcrap, crapstore, crapsite and b2bcrap—all .coms—are taken.
But to prove there is still an abundance of untaken names, here are just a few that remain unclaimed.
butthook.compalmhair.comhopeloss.comflyseason.comceleprosy.combuttsleeve.comworsestill.compalmnoogie.comdeerfillet.comstillstupid.orgweaselmeat.comisobozo.combobfromhell.comedgewrangler.comcoloncam.comspineshavings.comfrogdriver.combricktooth.comsmartweasel.comeyewax.com
—Doc Searls
A couple words from our resident linguist.
Tune in, turn on, click out.
What's the opposite of “sticky”? Try “clicky”. A clicky site is one with plenty of interesting hyperlinks to elsewhere. What better to support than curiosity?
A few weeks ago I was talking with Tim O'Reilly about the noun “information”, which lately has been replaced with “content”. Not that we've lost much. Both now carry the meaning of cargo: something we aggregate, store, move, address and deliver. Where we're moving, clearly, is away from real meaning.
Information, we noticed, derives from the verb inform, which derives from the verb form. In conversation, we don't just “deliver information” back and forth. We form each other. When I learn something new from you and what I learn is meaningful—that is, I can't forget it—you have literally formed me. In other words, we are authors of each other. What's more, we are in the market to be formed. We demand it. Otherwise, we wouldn't learn a damn thing.
That's why it's misleading to conceive of information as a substance we “deliver” to each other (or worse, to an “audience” of “eyeballs”). When we do that, we insult the verb at information's heart.
So how can we start to recover some of the meaning lost when information becomes content? I suggest abbreviating “information” to “of”. When we're in the market for something meaningful, we don't want content, or even information. We want the real deal, pure and uncut. Give us of.
Okay, “clicky” has a better chance. But time will of.
—Doc Searls
After a slight slip due to a strong Red Hat surge in April, Mandrake bounced back to increase its lead in Linux distribution downloads from Tucows in May. Measured through May 25, Mandrake was first with 40%, followed by Red Hat with 23%. That's a gain of 4% for Mandrake and a drop of 7% for Red Hat. Next was Corel, which dropped 2 to 10%. SuSE gained 2 and reached 5%. Slackware had 3%, FreeBSD had 2 and so did Phat, which continued its drop from a high of 13% in February. The rest were at 1% or less.
Now for an interesting statistical effect. Astute readers will remember that last month, Red Hat took the lead, with 33% to Mandrake's 31%. Like this month's May figures, April was then tabulated through only the first 25 days. What a difference just five days makes. In this month's report, we look at all 30 days of April, and the difference pushes Red Hat down 3% and Mandrake up 5%. This leaves Red Hat in second place and Mandrake in first: exactly the positions they've maintained since February. Tune in next month to see if those last five days make any difference in the final May numbers.
Web pages use a publishing metaphor. They are pages, after all. We write, open, read and bookmark them. That's one reason we assume that when a page downloads from a server, it's a one-way deal. The HTML describes the page, lays out the print, loads the graphics onto the page and into the cache.
There is at least the presumption of privacy. After all, reading is a personal (even an intimate) act. At times when interaction is required, such as filling out a form, there's a “submit” button that sends information back to the other end of the line. We're still in control.
And okay, we know about cookies and what they do. If we're especially vigilant, we either refuse to accept them, or we go through the whole pile and weed out the suspicious ones.
But watch out. Big Brander is watching you. And not just with cookies.
It turns out that some companies are spying on you and your web travels by using invisible 1x1-pixel transparent GIFs. These are in-line images downloaded from elsewhere, so the server-browser dialog can initiate covert reconnaissance on you and your subsequent surfage. You see no ad, and suspect nothing. The cookie alert doesn't go off. But the bug—as in bugging device—has been planted.
Who's doing the planting? Usually, a company that wants to learn something about you. Most of the time it's an advertising service that wants to “target” you with banners, e-mail spam or whatever. But they can serve all kinds of purposes, known and unknown. Don Marti found one on a Fed Ex page. (Presumably, they want to track customers the way customers want to track a package.) Richard Smith, the leading source of information on Web Bugs, found two on Quicken's home page, both providing “hit” information to advertising companies.
According to Smith's Web Bug FAQ www.tiac.net/users/smiths/privacy/wbfaq.htm, here is the information a Web Bug sends back to its server:
the IP address of the computer that fetched the Web Bug
the URL of the page the Web Bug is located on
the URL of the Web Bug image
the time the Web Bug was viewed
the type of browser that fetched the Web Bug image
a previously set cookie value
Of course, any graphic can serve the same purpose. That's why the only way you can see a Web Bug is to view a page's HTML source. But Smith also provides another way to at least discover what sites are playing slight-of-pixel games: The Web Bug Search Page, www.tiac.net/users/smiths/privacy/wbfind.htm. It shows where each of ten bugging companies are sneaking in their little spies. Makes for interesting (and creepy) reading.
On the matter of security, Don Marti gets the last word: “When a site tries to violate users' common-sense expectation of privacy, it should be the system administrator's responsibility to protect the user unless the user requests otherwise. Web ad banners are a security hole.”
—Doc Searls
When he was at Novell in the 1980s, Craig Burton changed the concept of networking by making Netware hardware-independent. Later, at The Burton Group, he drove a new understanding of networks—as services (file, print, directory, security, management) rather than “pipes & protocols”.
Lately, he has been turning his attentions to open source. He consults for a number of open-source companies, plus companies looking for open-source strategies. As always, his thinking is highly unique, independent and not part of anybody's orthodoxy. We caught up with him for a brief interview after he moderated a panel in April at Linux Journal's “Linux For Suits” event at Internet World. The interview moved forward by e-mail in May and June.
Doc: From what I gather, you like open source, but not the way we talk about it.
Craig: I recognize open source as a fact of business life that we need to get our heads around, but we won't make much progress until we start pulling apart a lot of distinctions that are currently collapsed. Until we do, “open source” will just be a buzz phrase instead of a fully rational strategy.
Doc: You mean for vendors?
Craig: I mean for every company that wants to operate in the world we're all trying to build here. If you want to survive in the long run, you need an open-source strategy. But you won't be able to implement one if you collapse a bunch of highly discrete distinctions.
Doc: Such as?
Craig: Accessibility and ownership. These are very different sets of distinctions, and they are entirely collapsed when most of us talk about them. The opposite of open is closed, not proprietary. The opposite of proprietary is public domain, not open.
Accessibility is an extremely important issue, and it is not just about source code. There are questions of source, binaries, licensing and derivative works. There are questions of protocols and APIs. There are questions of cost. It is important to make distinctions among the variables here. As an industry, we have collapsed the issues of accessibility and ownership.
Here is a matrix that separates those issues but keeps them in the same discussion by positioning them orthogonally. The accessibility axis runs from Closed to Open, while the ownership axis runs from Proprietary to Public Domain.
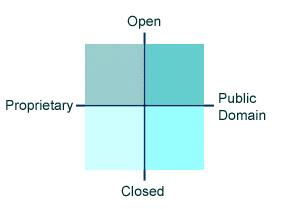
Figure 1. Burtonian Matrix
This is the matrix we need to understand, given any technology. Microsoft has reluctantly participated in the open-source corner of that matrix, and over time has moved a lot of technology into the open/public domain quadrant. And a lot of stuff they haven't. But the only significant difference between the Open Source community's products and Microsoft's is the amount of core technology that is made available in the open source half of that matrix.
Doc: So you don't believe that because most of Microsoft's familiar software is closed source, that it sucks?
Craig: First, some of it sucks and some of it doesn't. In spite of the open source movement, customers are buying it and using it. Further, there are other companies that have leveraged the Microsoft model to make money. On the other hand, there is the constant threat to customers that Microsoft will try to lock them in, and there is the constant threat to Independent Software Vendors (ISVs) that Microsoft will encroach on their businesses. Despite these threats, however, the industry continues to grow and thrive. As a model for making money—for lots of companies—we have seen nothing comparable yet from the Open Source world.
Doc: But we have seen a number of money-making models outlined by Eric Raymond, first in “The Magic Cauldron” and then in the book version of The Cathedral and the Bazaar.
Craig: Yet by Eric Raymond's own description (in “Homesteading the Noosphere”), an anti-commercial bias is part of the “hacker ideology” out of which the Open Source movement has grown. That's one reason that the distinction he makes between a cathedral and a bazaar is more accurately one between a cathedral and a cult. A bazaar is, if nothing else, a marketplace. And marketplaces are by definition hospitable to business. So the culture of Open Source has a strong steak of inhospitality to business. A lot of this comes from the original Free Software movement and persists as a legacy in the GPL license, which is in many ways the least open and business-friendly of all the open-source licenses certified by Eric's organization, the Open Source Initiative. The main reason I point this out is that this anti-commercial bias accounts for the collapsing of distinctions here, because this bias introduces a third axis—a moral one that runs from bad to good. You can see it running from the lower left to the upper right. Proprietary and Closed are Bad. Open and Public Domain are Good. This is fine if all you want to do is hack code. But if you want to do business, you've got to face rational choices that are all over this matrix, whether you're a supplier or a customer.
Doc: Did I hear you say that the GPL is really a moral statement?
Craig: Moral and political. To me, the GPL is as much a political statement as a licensing agreement. There's a bunch of stuff in there that's superfluous to licensing concerns. This mixing political with licensing views is what causes businesses to be suspicious of open source.
Doc: But historically, the Open Source movement has tried to move away from the Free Software movement's anti-commercial rhetoric and policies.
Craig: Absolutely. The Open Source movement has a tall order, in attempting to commercialize the Free Software movement. We owe a lot to Eric Raymond for attempting to make free software palatable to business—and succeeding. Now it's clear that Open Source is a movement that will eventually include everybody. But that doesn't mean all the code in the world will be open source. Or public domain.
Doc: The important thing, then, is that both suppliers and customers need to factor open source into their strategies.
Craig: Exactly. Every business needs an open-source strategy. But the choices should not—and will not—be made on moral grounds. There are many combinations of choices that are all over this map. And you see them when you look at some of the relatively proprietary and/or closed products, or product components, being sold by card-carrying members of the Open Source community.
Doc: Such as all three desktop office suites for Linux. Applix, Sun and Corel all make closed-source suites.
Craig: Exactly. And they're all clones of Microsoft Office to a significant degree. But let's stay with the core issue here. Software varies greatly in accessibility, and open source isn't the only variable. In many cases, you can get at the APIs but not the source code. That makes the software somewhat more open than if the APIs and the source were closed. Beyond the API, there is the case—as in the UDA for Microsoft—where customers and competitors can add value to the Microsoft model without having source.
Doc: Do you think Microsoft has any understanding of this matrix, or uses it strategically?
Craig: In fact, Microsoft has moved quite a few things to the upper-right quadrant of the matrix. The Universal Data Access model provides a framework for accessibility to core Windows constructs. UDA is not open-source-based, but it provides programmatic interoperability with the Windows architecture. While I think Microsoft could do a lot more—including providing an open-source-based strategy to make Windows accessible—it has made large strides to open up Windows, and we shouldn't ignore that fact for the simple reason that developers and customers have taken advantage of it. Many, many companies have figured out how to make money off of Microsoft's accessibility model.
Doc: But can Microsoft have a truly strategic open-source strategy if it is hostile to open-source software and the Open Source movement?
Craig: No, it can't. Microsoft's combativeness, its hostility to everything it perceives as a threat, works against it here. But the same thing goes for the combative folks in the Open Source community. Both sides fail to understand the reasons for the other's successes. We have to get past that, and a good way to start is by getting clear about what some of these distinctions really mean. Without that clarity, we see gray as black or white.
Doc: How, for example?
Craig: Many Linux distributions are chock full of stuff that's both closed and proprietary. We just excuse it because it's bundled with something that is called “open”. We see gray as white. Good guys wear white hats and sell white code. But that's not always the case.
Doc: Give me an example of closed source code that passes for open.
Craig: Security components that use PKI—Public Key Infrastructure. We're talking about copyrighted, patented stuff. Proprietary and closed as can be.
Doc: You mean RSA?
Craig: Right. The distributions can't open source the RSA code. And it's all over the place.
Doc: Let's go to the big picture here. I watched you change the whole networking conversation back in the '80s, from one about wires and protocols to one about services. Are we at a similar cusp at this point in time?
Craig: Yes. For some reason, there's this idea that the Net is a finished thing. In fact, it's only beginning. One of its virtues is that it's still wide open. And it would help if more of us understood that openness—the ability of infrastructural software to interoperate without interference from anybody's agenda—is what enables growth. Over time, as Microsoft is discovering, the challenge is moving infrastructural code to the upper-right corner of this matrix. There is a big movement right now to copyright and patent everything you can name, but in the long run, that's wasted effort. It's more rocks in the stream of progress. History will flow around these obstacles. The real question companies need to ask is not “how do we patent and copyright and protect our stuff” but “how do we make money and do business while we gradually move toward that upper-right quadrant?” To do that, you need to see the Net as something that still desperately needs a lot of infrastructure.
Doc: Such as?
Craig: Directory and security services, which go hand in hand, are still very primitive. The Linux community is still using Sun's yellow pages (now called NIS) for directory services. Within Linux itself, it's old UNIX legacy stuff that hasn't changed in many years. Before we can have real privacy, and real secure communication, and real useful directory services—which we'll need to keep track of a world of abundant, changing and distributed objects—we're going to have to evolve past that legacy.
Doc: Novell wants us to use NDS. Microsoft wants us to use Active Directory.
Craig: And neither will be adopted by the Linux community, which is necessary for this whole thing to move forward. They're both proprietary and in the way. Rocks in the stream.
Doc: How do you conceive the Net? What's its conceptual architecture?
Craig: I see the Net as a world we might see as a bubble. A sphere. It's growing larger and larger, and yet inside, every point in that sphere is visible to every other one. That's the architecture of a sphere. Nothing stands between any two points. That's its virtue: it's empty in the middle. The distance between any two points is functionally zero, and not just because they can see each other, but because nothing interferes with operation between any two points. There's a word I like for what's going on here: terraform. It's the verb for creating a world. That's what we're making here: a new world. Now the question is, what are we going to do to cause planetary existence? How can we terraform this new world in a way that works for the world and not just ourselves? Remember, this thing is in outer space. It's not connected to anything else. If you want to live here, you have to bring your own sustaining structures, foods and the rest of it.
Doc: Is this something like what Larry Lessig calls “end to end” architecture?
Craig: I haven't read much of Lessig's work yet, but I believe we're consistent here. But since we're talking about authors, I also like Carl Shapiro and Hal Varian's Information Rules, which makes pragmatic distinctions between the economy of building things and the economy of building information. The old economy was driven by economies of scale, including time, resources and materials. The Open Source community claims this is outdated, and they're right. But now what? These guys say that the economics of information invite respect for network effects, which can be increased by leveraging the value of intellectual property, rather than by protecting that property. A key to understanding the economies of networks is seeing that networks are comprised of relationships. That favors companies that build and maintain relationships through one of your favorite subjects: conversations.
Doc: Who are going to be the leaders in your view of the Web?
Craig: I have six theses—as opposed to ninety-five—that I use as the basis for determining the leadership of the next-generation web companies:
No single vendor can own the web infrastructure. Therefore, inclusion is imperative.
Distinguish accessibility from ownership.
Standards are independent from these distinctions.
The market drives accessibility requirements, not by credo, license agreements or moral positions.
An open-source-based model requires all core technology to become more accessible over time.
Those who—pragmatically and not moralistically—know when to put what in the upper half of the matrix will define leadership of the next generation of the web. --Doc Searls
Web pages use a publishing metaphor. They are pages, after all. We write, open, read and bookmark them. That's one reason why we assume that when a page downloads from a server, it's a one-way deal. The HTML describes the page, lays out the print, loads the graphics onto the page and into the cache.
There is at least the presumption of privacy. After all, reading is a personal (even an intimate) act. At times when interaction is required, such as when we fill out a form, there's a “submit” button that sends information back to the other end of the line. We're still in control.
And okay, we know about cookies and what they do. If we especially vigilant, we either refuse to accept them or go through the whole pile and weed out the suspicious ones.
But watch out. Big Brander is watching you. And not just with cookies.
It turns out that some companies are spying on you and your Web travels by using invisible 1x1 pixel transparent GIFs. These are in-line images downloaded from elsewhere, so the server-browser dialog can initiate covert reconnaissance on you and your subsequent surfage. You see no ad and suspect nothing. The cookie alert doesn't go off. But the bug—as in bugging device-has been planted.
Who's doing the planting? Usually a company that wants to learn something about you. Most of the time it's an advertising service that wants to “target” you with banners, e-mail spam or whatever. But they can serve all kinds of purposes, known and unknown. Don Marti found one on a Fed Ex page. (Presumably they want to track customers the way customers want to track a package.) Richard Smith, the leading source of information on Web Bugs, found two on Quicken's home page, both to provide “hit” information to advertising companies.
According to Smith's Web Bug FAQ www.tiac.net/users/smiths/privacy/wbfaq.htm, here is the information a Web Bug sends back to its server:
The IP address of the computer that fetched the Web Bug
The URL of the page that the Web Bug is located on
The URL of the Web Bug image
The time the Web Bug was viewed
The type of browser that fetched the Web Bug image
A previously set cookie value
Of course any graphic can serve the same purpose. That's why the only way you can see a Web bug is to view a page's HTML source. But Smith also provides another way to at least discover what sites are playing slight-of-pixel games: The Web Bug Search Page www.tiac.net/users/smiths/privacy/wbfind.htm. It shows where each of ten bugging companies are sneaking in their little spies. Makes for interesting (and creepy) reading.
On the matter of security, Don Marti gets the last word: “When a site tries to violate users' common-sense expectation of privacy, it should be the system administrator's responsibility to protect the user unless the user requests otherwise. Web ad banners are a security hole.”
—Doc Searls
Percentage of public relations professionals who admit to lying on the job: 25
Percentage of public relations professionals who say they are not always able to confirm the validity of information conveyed to reporters on behalf of clients: 62
Percentage of web sites with personal server headers: 5.7
Number of Linux servers that self-disclose their distribution brand: 0
Number of Linux servers found by Netcraft to disclose their distribution through Apache's personal server header: 850,000
Percentage of those servers that identify their distribution as Red Hat: 72
Percentage of those servers that identify their distribution as SuSE: 10
Percentage of those servers that identify their distribution as Debian: 9
Number of other distributions with more than 3%: 0
Market cap of the entire Linux category in July 1999: $0
Market cap of Red Hat at its peak in November 1999: $22.5 billion
Red Hat revenues in the quarter ending November 1999: $5.7 million
Market cap of Red Hat on June 1, 2000: $2.8 billion
Red Hat revenues in the quarter ending February 2000: $13.1 million
Market cap of thirteen “Tier 1” Linux companies on June 1, 2000: $8 billion
Percentage of girls at popular teen web site who say they have had sex by the age of fifteen: 35
Percentage of girls at popular teen web site who say virginity is in: 34
Percentage of visits to popular teen web site that use Linux: .22
1-2: PRWeek, according to Reuters
3-9: Netcraft, http://www.netcraft.com/
10-15: Linux Weekly News and public financial information sources
16-18: http://www.smartgirl.com/
What were people talking about in May and early June? Below is a sampling of some of the hotter news stories over the past few weeks, as reported in “The Rookery”, Linux Journal's on-line source for news, notes, quotes and reports from the field (updated daily and found at our web site, http://www.linuxjournal.com/):
Python moves to BeOpen.com, and Guido van Rossum is appointed director of PythonLabs.
Gateway and AOL become Transmeta's first big-time customers. Look for a variety of Internet devices running on the Crusoe chip later this year.
Google adopting Linux as its operating system of choice.
Microsoft being given the OK to tie up the court system in years upon years of appeals, trying to avoid the break up.
Loki Entertainment Software releases Descent 3.
The European Union looks to be more strict with software patents.
Kevin Mitnick being courted as security advisor.
Poor Corel!
Debian's General Resolution, an amendment to the Debian Social Contract, which hopes to minimize the impact of non-free software on Debian GNU/Linux.
Linux being pre-installed on the IBM ThinkPad.
InterBase 6 is out, and the cross-platform relational database is now officially in the Open Source world. The source code has been released and so has a new company by the same name, created for the purpose of serving the businesses that put InterBase code to use.
The president of the new company is Ann Harrison, who co-founded the original InterBase with Jim Starkey, the product's original creator. Starkey also has a position with the new company as “technology software architectural advisor”. This allows him to work inside the Open Source development community that began growing around InterBase even before the code was released.
Back in January, after Inprise (a.k.a. Borland) promised to open source InterBase, Linux Journal interviewed Inprise CEO Dale Fuller on the subject. That interview drew a record response from readers, most of whom expressed enthusiasm for the move. Since then, interest in InterBase has grown, while both Inprise and InterBase have gone through a number of gyrations.
The intent to spin out a new company was announced in February, around the time Inprise announced plans to merge with Corel. Interest in InterBase grew, while the nascent company labored to craft both a business plan and a licensing strategy. The merger was called off in May, by which time free InterBase binaries were being downloaded at the rate of 3,000 per week (that's more than 50,000 as of late June).
By July, however, the new company was moving forward. “Basically, we're a start-up,” Ann Harrison says. The company is 19% owned by Inprise/Borland's venture fund and expects to grow quickly, along with the adoption curve of Linux in enterprise, which is moving rapidly. “Linux is a phenomenon much like the Internet five years ago, and it's bringing up a lot of the same kind of easy choices,” Harrison says. “People will say, `Why should I bother fighting with the file system and trying to write my own index code? Here's this free database. It just works. Why don't I pick that up and use it?”' Suddenly, it becomes the default way of storing data.
The business model is to sell add-ons and services around the product. These include training, support, documentation and third-party packages such as an ODBC driver, a Java driver and a product for connecting with development tools. The company does not plan to do any development of its own, but instead serve and back InterBase development and deployment, by both the development community and enterprise customers.
Kylix will help. Kylix is the code name for Inprise/Borland's family of visual development tools for Linux, due for release this summer. “We have a lot of tools that work well with Kylix, so when it's released, that will give us another boost,” Harrison says.
The company's goal is not modest. “Some day there will be a popular spreadsheet for Linux desktops, with lots of users in the enterprise. Where will that data live? On InterBase, we expect. Our goal is not to own an organization, but rather to own all the organization's applications, from the standpoint of the data store.”
While InterBase never scored big as a commercial product, it did develop a loyal following over the years starting in 1984, when the company was founded on an idea Jim Starkey had in the shower, and initial capitalization of $243.50. After early success with selling to the UNIX workstation market, the company was sold to Ashton-Tate, which was sold to Borland, which became Inprise (now Inprise/Borland, or vice versa—it's hard to keep the old name down). Restarting the same company with two of the founders is an interesting second-chance story.
InterBase does face competition in the category. PostgreSQL has been open source for many years, and also has a loyal following. And the incumbent relational databases are certainly not going to go away easily.
But Linux is being adopted quite easily by countless enterprises. If InterBase can surf that wave, it should do pretty well.
—Doc Searls