
The TCP/IP stack (of protocol-drivers that comprise the TCP/IP support in your kernel) differentiates between different network applications and sessions by port numbers. Each type of application/dæmon/process that needs to accept connections via the TCP or UDP protocol is assigned a port number.
These are numbered 0 through 65,536, and there are two sets: one for TCP, one for UDP. In other words, the port TCP 2,000 can be used by one process and UDP 2,000 can be used by another (assuming, of course, that process #1 uses the TCP protocol and process #2 uses UDP).
Ports 0 through 1,023 may be used only by processes running with root privileges and are therefore called system ports or privileged ports. The Internet Assigned Numbers Authority (IANA) maintains a list of official port-number assignments: telnetd more or less universally uses TCP 23 because IANA says it should.
Note that as with so many other aspects of the Internet, this is a convention rather than international law: there's nothing to stop a programmer from writing, for example, a non-Telnet application that uses TCP 23. Still, if you scan a host and find that TCP 23 is active, it's a pretty safe bet that a Telnet dæmon is listening there.
Ports 1,024 through 49,151 can be used by non-root privileged processes, are also registered by IANA (as “a convenience to the community”), and are known as the registered ports. Ports 49,152 through 65,535 can be used for private (non-internet-connected) or dynamically assigned processes and are therefore called dynamic or private ports.
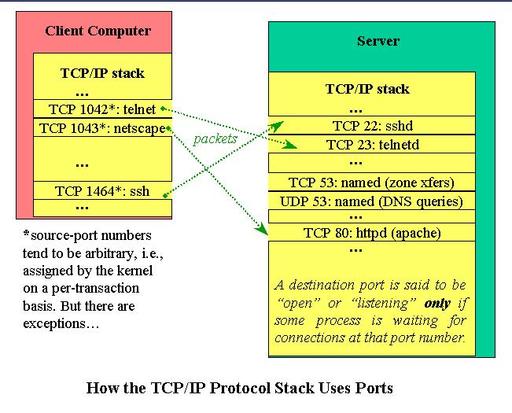
The last bit of TCP/UDP port trivia you may be interested to know is the difference between source ports and destination ports. Each TCP or UDP packet has both a destination port (i.e., the port number to which that packet is being sent) and a source port (i.e., the port number from which that packet's originating process sent the packet, and to which the remote service/dæmon's replies should be sent).
Unlike destination ports, source ports are usually, depending on the application, dynamically assigned on a per-transaction basis by the kernel. The list of port assignments and services in your system's /etc/services file then applies only to local listening/destination) ports (e.g., telnetd) and not to the source ports of local outbound client processes (e.g., Telnet).
Some applications such as NFS and NIS use dynamic destination port assignments too, but that's another subject.