
For privacy, windows have blinds, and Internet users have the Tor browser bundle.
I don't know how many readers know this, but my very first Linux Journal column (“Browse the Web without a Trace”, January 2008) was about how to set up and use Tor. Anonymity and privacy on the Internet certainly take on a different meaning in the modern era of privacy-invading software and general Internet surveillance. I recently went back and read my original column, and although the first few paragraphs were written six years ago, they seem just as relevant today:
Is privacy dead? When I think about how much information my computer and my gadgets output about me on a daily basis, it might as well be. My cell phone broadcasts my general whereabouts, and my Web browser is worse—every site I visit knows I was there, what I looked at, what browser and OS I use, and if I have an account on the site, it could know much more.
Even if you aren't paranoid (yet), you might want to browse the Web anonymously for many reasons. For one, your information, almost all of it, has value, and you might like to have some control over who has that information and who doesn't. Maybe you just want to post a comment to a blog without the owner knowing who you are. You even could have more serious reasons, such as whistle-blowing, political speech or research about sensitive issues such as rape, abuse or personal illness.
Whatever reason you have for anonymity, a piece of software called Tor provides a secure, easy-to-setup and easy-to-use Web anonymizer. If you are curious about how exactly Tor works, you can visit the official site at tor.eff.org), but in a nutshell, Tor installs and runs on your local machine. Once combined with a Web proxy, all of your traffic passes through an encrypted tunnel between three different Tor servers before it reaches the remote server. All that the remote site will know about you is that you came from a Tor node.
The rest of the article went into detail on how to use the Knoppix live disk to download and install Tor completely into ramdisk. Tor has come a long way since those days though, so I decided it was high time to revisit this topic and explain the best way to set up Tor on your personal machine today.
In the past, Tor installation meant installing the Tor software itself, configuring a proxy and pulling down a few browser plugins. Although you still can set it up that way if you want, these days, everything is wrapped up in a tidy little package called the Tor browser bundle. This single package contains Tor, its own custom Web browser already configured with privacy-enhancing settings and a user interface that makes it easy to start and stop Tor on demand.
The first step is to visit https://www.torproject.org and check the lock icon in your navigation bar to make sure the SSL certificate checks out. If your browser gives you some sort of certificate warning, it's possible you aren't visiting the official Tor site, and you should stop right there and attempt to get Tor from a different computer. On the main page is a large Download Tor button for you to click. If you are browsing the site from a Linux system (which of course you are), you will be presented with links to a 32-bit and 64-bit browser bundle package, so click the one that corresponds with the appropriate architecture for your system.
While the software downloads, I highly recommend you do two things. First, next to the button you clicked to download Tor, there should be a hyperlink labeled “sig”. Click this link to download the signature you will use to verify that the Tor package you downloaded was legitimate (I'll talk about how to do that in a minute). The second thing you should do is scroll down the page and start reading the section titled “Want Tor to really work?” to familiarize yourself with some of the extra habits you should take on if you really do want to browse the Web anonymously.
After you download the Tor browser bundle and the signature file, you should have two files in your directory:
tor-browser-gnu-linux-x86_64-2.3.25-14-dev-en-US.tar.gz
tor-browser-gnu-linux-x86_64-2.3.25-14-dev-en-US.tar.gz.asc
The first of these files is the software itself, and the second file is the GPG signature. Although a lot of software uses MD5 or SHA1 checksums so you can validate the software you downloaded was complete, this checksum is different. The .asc file is a cryptographic signature you can use to prove that the software you just download actually was provided to you by the Tor project and not by some malicious third party. The site provides documentation on how to verify this signature for different operating systems at https://www.torproject.org/docs/verifying-signatures.html.en, but since you use Linux, here you will run the following commands. First, pull down the key that was used to sign this package. Currently, this would be Erinn Clark's key (0x416F061063FEE659), which you can import with the following command:
$ gpg --keyserver x-hkp://pool.sks-keyservers.net ↪--recv-keys 0x416F061063FEE659
Once the key has been imported, you should check its fingerprint:
$ gpg --fingerprint 0x416F061063FEE659
pub 2048R/63FEE659 2003-10-16
Key fingerprint = 8738 A680 B84B 3031 A630 F2DB 416F 0610 63FE E659
uid Erinn Clark <erinn@torproject.org>
uid Erinn Clark <erinn@debian.org>
uid Erinn Clark <erinn@double-helix.org>
sub 2048R/EB399FD7 2003-10-16
If the fingerprint doesn't match what you see above, something fishy is going on and you shouldn't trust this package. Of course, if you are frequent GPG users, you may want even better assurances. Hopefully, you have someone you already trust within your GPG keyring who has been to a key-signing party with Erinn Clark. If so, it would help validate that the key is legitimate.
Once you have validated the fingerprint, cd to the directory that has the browser bundle and .asc file, and run the following command:
$ gpg --verify
↪tor-browser-gnu-linux-x86_64-2.3.25-14-dev-en-US.tar.gz{.asc,}
gpg: Signature made Fri 01 Nov 2013 01:25:10 PM PDT
↪using RSA key ID 63FEE659
gpg: Good signature from "Erinn Clark <erinn@torproject.org>"
gpg: aka "Erinn Clark <erinn@debian.org>"
gpg: aka "Erinn Clark <erinn@double-helix.org>"
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature
↪belongs to the owner.
Primary key fingerprint: 8738 A680 B84B 3031 A630
↪F2DB 416F 0610 63FE E659
If the output says “Good signature”, everything checked out. Again, you will see a warning if you don't have someone in your chain of trust that already trusts this key.
At this point, it's relatively trivial to install and use Tor. Just use tar to extract the .tar.gz file into your home directory or wherever else you'd like it to be, and then run the start-tor-browser script inside:
$ tar zxvf tor-browser-gnu-linux-x86_64-2.3.25-14-dev-en-US.tar.gz $ ./tor-browser_en-US/start-tor-browser
You should see a GUI window pop up that looks like Figure 1.
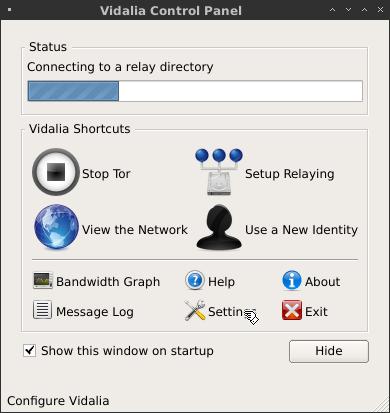
Figure 1. The Vidalia Control Panel Window
It may take a little time for your Tor network to finish configuring, but once it does, you will know, because a browser that looks like Figure 2 will appear.
The initial Tor check page not only validates that you are using the Tor network, it also displays your current IP address. If you ever notice that IP address matches your home IP address, or if you don't see this congratulations window at all, for some reason your Tor instance isn't working properly, so you shouldn't do anything within the browser that is privacy-sensitive. Note that because you may be exiting the Tor network from an exit node in a different country, certain sites like Google, for instance, that try to be helpful and display the site in a country's native language may present you with Japanese, German or some other language as you visit.
If you go back to the Vidalia Control Panel, you'll notice a number of different options. You can view a map of the current global Tor network; you can click the Setup Relaying button to add your machine to the network of Tor nodes, and if you click Use a New Identity, you will stop using the three Tor nodes you currently are using and will set up a new connection with different Tor nodes. Although Tor itself does this routinely as you use it, sometimes you may want to get a different endpoint so a Web site stops displaying output in a language you don't understand.
It's important to note that this special Tor browser has been configured with extra plugins and settings to enhance your privacy. For instance, by default, the Noscript plugin is installed and enabled, which blocks JavaScript, Java and other plugins and allows them only for sites that you trust. The browser also includes the HTTPS Everywhere plugin that defaults to using HTTPS for any site you try to visit. You also will see a small onion icon in the navigation bar that you can use to tweak your Tor preferences inside the browser.
Once you are done browsing anonymously, close your browser and go back to the Vidalia Control Panel. If you are done using Tor completely, click the Stop Tor button, and then click exit to close the application. Browsing the Web anonymously and privately has never been this easy.