
Make your accounts more secure with two-factor authentication!
Last weekend my work phone suddenly stopped working. Not the phone itself, but rather all service stopped. I first noticed (of course) due to an inability to load any web pages. Then I tried calling someone and realized my phone was disconnected. In fact, when someone tried to call me, it said the line was no longer in service. It was Sunday, and my phone is a company device, so I had to wait until Monday to get things sorted.
It turns out someone called in to Verizon claiming to be me. The individual claimed his phone (my phone) had been stolen, and he wanted to transfer service to another device. He had enough information about me to pass whatever verification Verizon required, and if he'd been a little smoother on the phone, he'd have likely gotten my number. It turned out that the Verizon employee felt the call was suspicious and disabled the account instead of transferring service. (I know that only because the employee made a note on the account.) After a stressful day of back and forth, the company I work for was able to get my phone turned back on, and I still have the same phone number I've always had—thank goodness.
Kyle Rankin saw me tweet about my phone issues, and he immediately responded that I should check my online accounts, especially those with two-factor authentication. If other people had been able to get my phone number, they could use that as “proof” of their identity and reset many of my passwords. It hadn't occurred to me just how much we depend on our cell-phone companies for security, even on our personal bank accounts. That doesn't mean two-factor authentication (2FA) isn't important, it just means we need to consider our phones as a viable vector for attack. So in this article, I want to talk about securing your online accounts.
Before I talk about securing online accounts, I urge you to contact your cell-phone company. I use several providers myself, and after my experience with the company phone, I realized just how important it is to contact the provider and set up security. By default, your cell-phone company might have a few security questions for you to answer. It also might just ask for your date of birth in order to access account information. It's important to call and ask what sort of security you can add to the account to make sure a third party can't pretend to be you. What that security looks like will be different for every company, but really, call them. Anyone on Facebook can look up my birthday, and if that's all you need to make changes to an account...well, yikes.
Once you're confident that your phone isn't easily compromised, it's time to start looking at your online accounts. Not all businesses provide two-factor authentication, but more and more are adding the service every day. Even if your banks, email accounts and Spotify stations don't have extra layers of protection, having a good password is crucial.
I've written in the past about creating “good” passwords. Some of what I recommended is valid, and some was shortsighted. I was in good company with my shortsightedness, because tons of companies still require “complex” passwords. The problem is, password complexity generates passwords that are hard for humans to remember and easy for computers to guess. The famous xkcd comic explains the problem much better than I can (Figure 1).
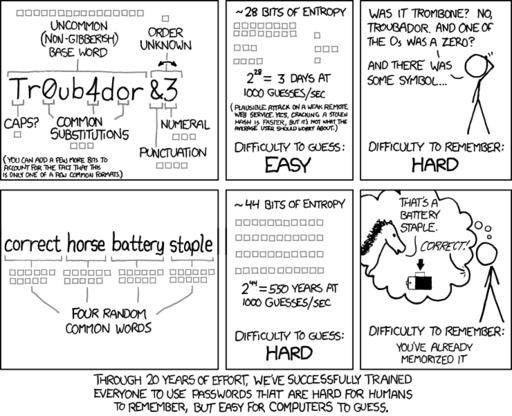
Figure 1. This comic titled “Password Strength” from xkcd is so true it hurts (https://xkcd.com/936).
(Note: Randall Munroe from xkcd.com made it fairly clear that occasionally reprinting his comics is okay as long as he is attributed. I'll go so far as to say not only is his work awesome, but you should go buy things from his store. Seriously, he's awesome.)
The problem with truly “good” passwords is that they rarely meet the requirements for complexity that most websites demand. It seems like companies are perfectly fine with an eight-character password, as long as there's a capital letter, punctuation, a number and no common words. Basically, they demand we have crappy, hard-to-remember passwords. It's very frustrating.
If you're not using a password manager that generates random passwords, the best I can recommend is that you make your password as long as possible. My method for making a password is to string together words (like correcthorsebatterystaple, which I didn't even have to look up, because I totally remembered it), and then add the weird complexity requirements at the end. That still doesn't help with password reuse, however, which is an even bigger problem than using strong passwords. Again, Randall illustrates the problem perfectly at https://xkcd.com/792. (I'm just giving a link this time; I don't want to push my luck.)
Basically, if you use the same password everywhere, if one system is compromised, all your accounts are vulnerable. I addressed that problem in my last article about setting up good passwords, but unfortunately, any pattern you might use to create passwords can be figured out. Here's what I mean. Let's say you use this pattern for generating passwords:
word1 word2 sitename word3 word4 complexity_junk
On the surface, this seems brilliant. You can remember four words, have a standard “complexity” ending for meeting dumb password requirements, and you can add the name of the website in the middle. That means every password will be different. The problem is, it's still a pattern. Let's say an attacker discovers that your Facebook password is this:
hampergranitefacebookcoffeeostrich53BLT!
That's a nice, long, unique password. The problem is, now the attacker knows your Amazon password is this:
hampergraniteamazoncoffeeostrich53BLT!
Truly, the best method I know of is to have a password manager that will store and potentially generate passwords for you. I prefer passwords I don't have to copy/paste in order to use, so I usually generate long passwords using words. That way, I can glance at the password and type it out quickly. The point of this whole section is to make you think about passwords. Consider passwords that are truly strong, but also remember that it's extremely important not to reuse passwords on multiple sites.
Two-factor authentication comes in many flavors. For cell phones, the trend is to use fingerprints. Granted, fingerprints aren't the most secure authentication method, but when used in addition to passwords, it does add significant security. (I once heard Kyle Rankin say fingerprints are terrible passwords, because you can change your “password” only ten times, and you leave them written everywhere you touch.)
The cell-phone number itself is one of the most common forms of 2FA. Like my original example demonstrated, many websites utilize SMS messages sent to a phone number as verification of identity. There are many issues with an SMS being the sole form of authentication, but as a required second factor, it's not bad. What I mean by that is, many companies allow you to use your cell phone for 2FA, but they also allow you to recover your password by simply proving who you are by entering a code sent via SMS. That completely eliminates the security of 2FA!
My personal favorite 2FA method is provided by Google. The implementation is fairly robust, and in function, it's very easy to use. Basically, you authenticate your phone, and rather than having a code texted to you, which you have to type into a web form, the Google authenticator just pops up on your phone asking if you're currently trying to log in (with information on where you're trying). You simply click “yes”, and the 2FA is successful. I like it not only for simplicity, but also because my phone number being hijacked doesn't automatically give the thief the ability to provide 2FA.
There certainly are other methods for attaining multiple authentication factors. Yubi is a company that has provided hardware-based USB authentication for years. The problem I usually have is not everywhere supports multiple forms of 2FA. However, if a website allows you to log in with your Google account, Google handles the 2FA, thus securing the site without any custom-2FA code on the particular site at all.
Part of me dislikes recommending Google as your go-to source for 2FA. Google is a commercial company, and using its proprietary system as a form of authentication is a little unsettling. But here's the deal: I'd rather everyone trust the integrity of Google than trust the integrity of random hackers on the internet. Google's 2FA is easy to set up, has proven to be reliable, and at the very least, it's better than not using 2FA at all. So if you're interested in continuing down the Google rabbit hole, I highly recommend you go through its security wizards to make sure your account is yours.
Head over to https://accounts.google.com (Figure 2). On the left, you'll see sign in and security options. This page is also where you can configure your privacy settings and recent activity. But for this article, I'm focusing on the sign-in and security page. Figure 3 shows when your password was last changed, whether or not 2FA (Google calls it two-step verification) is turned on, and whether you have any app passwords. You also can set up your account recovery information on this page, providing alternate email, phone number and secret questions.
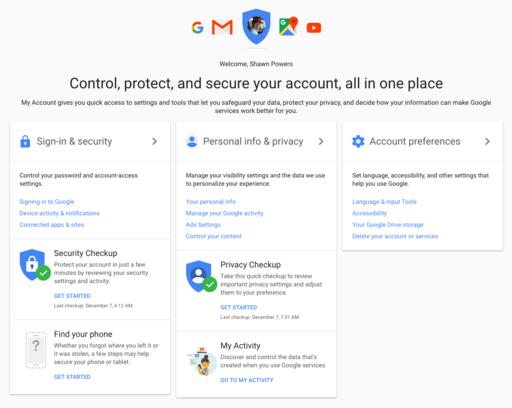
Figure 2. Follow all these links. The checkups are very useful, and it's better to over-prepare than under-prepare.
When you turn on 2-step verification (Figure 4), you're able to configure multiple 2FA options and set a default. I use the Google Prompt (described previously) as my default method, but I also have my phone number as an option. Plus, Google allows you to configure a number of alternates like a USB hardware key, printable offline codes and an authenticator app that will generate 2FA codes even while your phone is offline. Truly, it's the variety of options that makes me love Google for my 2FA needs.
Ultimately, I urge you to set up 2FA on as many sites as support it. Most sites still require you to use SMS as the second factor, so be sure your phone number is secure (remember to contact your cell-phone provider). If websites support Google for 2FA instead of SMS, I personally recommend it. It's simpler, and that means you're actually more likely to use it. But whatever method you choose, 2FA is a good thing.
I use a password manager. I've used several through the years, but I do find having a secure database of passwords is helpful. If I'm being completely honest, none of the password managers I've tried are perfect. It's often cumbersome to get the password (especially hard-to-type passwords) from the manager to the website where you need it. Plus, going between desktops and mobile devices is always a challenge. I use LastPass, but it's not a perfect solution, and it's not free for mobile devices. There are open-source password management tools like KeePass, Padlock and Passbolt, but I've yet to find the perfect solution. If you have a password management system that works across platforms and devices in a convenient, yet secure way, please let me know. I'd love to write about it.
So, the moral of the story is to make sure your phone is secure, and then make sure your accounts are secure too—preferably with multiple factors of authentication. At the absolute least, please don't use the same password for multiple websites!