
Although your phone is probably the biggest threat to your privacy, your web browser is a close second. In the interest of providing you targeted ads, the web is littered with technology that attempts to track each site you go to via a combination of cookies and JavaScript snippets. These trackers aren't just a privacy threat, they are also a security threat. Because of how ubiquitous these ad networks are, attackers have figured out ways to infiltrate some of them and make them serve up even more malicious code.
The good news is that a series of privacy plugins work well with Firefox under Linux. They show up as part of the standard list of approved add-ons and will help protect you against these kinds of threats. Many different privacy plugins exist, but instead of covering them all, in this article, I highlight some of my personal favorites—the ones I install on all of my browsers. Although I discuss these plugins in the context of Firefox, many of them also are available for other Linux browsers. Because all of these plugins are standard Firefox add-ons, you can install them through your regular Firefox add-on search panel.
The EFF has done a lot of work recently to improve privacy and security for average users online, and its Privacy Badger plugin is the first one I want to cover here. The idea behind Privacy Badger is to apply some of the tools from different plugins like AdBlock Plus, Ghostery and others that inspect third-party JavaScript on a page. When that JavaScript comes from a known tracking network or attempts to install a tracking cookie on your computer, Privacy Badger steps in and blocks it.
If so many other plugins do something similar, why re-invent the wheel with Privacy Badger? Well, the downside to many of the other tools is that they often require user intervention to tweak and tune. Although it's great for people who want to spend their time doing that, average users probably rather would spend their time actually browsing the web. Privacy Badger has focused on providing similar protection without requiring any special tweaking or tuning. As you browse the web, it keeps track of these different sites, and by observing their behavior, decides whether they are tracking you.
So once you install Privacy Badger, how do you know it's working? For starters, after the plugin is installed, you'll see a new icon of a cartoon badger head in your Firefox task bar (Figure 1). Above that icon is a green, yellow or red box that contains a number. If Privacy Badger didn't have to block anything on a site, you'll see a nice green 0 in the box. On the other hand, if you see a yellow or red box, Privacy Badger flagged parts of the site, and if you click the icon, you'll see a list of the sites along with a rating. If a site is flagged as yellow, it means Privacy Badger thinks it might be trying to track you, but its cookies seem necessary for the functioning of the site so it has allowed them. On the other hand, if something is red, it means Privacy Badger has blocked it completely.

Figure 1. Privacy Badger (By Electronic Frontier Foundation https://www.eff.org/sites/all/themes/badger/badger-stroke.png, CC BY 3.0 us, https://commons.wikimedia.org/w/index.php?curid=42161849)
Ad trackers are obvious threats to your privacy, but there also are threats that might be less obvious. One big way you can be tracked is through your use of unencrypted traffic over HTTP. When you visit a site with HTTP, someone sitting between you and the site can capture a copy of your traffic and forward it on to the site. This is a particular risk if you are using a public network, like at a coffee shop or a conference. The solution is to make sure you visit sites only over HTTPS. By using HTTPS, you not only encrypt all of the traffic between your browser and the site, the site also will authenticate itself to you with a certificate so you can be sure you are talking directly to it and not to an attacker in the middle.
Because browsers default to HTTP, practically speaking, it can be difficult to add "https://" in front of every URL you type, especially when you consider how rarely you might even enter a URL in your browser these days. Plus, many sites default to HTTP even if they support HTTPS. Fortunately, the EFF saves the day again with its HTTPS Everywhere plugin. The HTTPS Everywhere plugin changes the default behavior in the browser so that when you visit a site, it attempts to connect to HTTPS first. Only after an HTTPS connection fails will it fall back to HTTP.
In addition to favoring HTTPS over HTTP, you can click the S icon in the blue box on your taskbar to see extra HTTPS Everywhere settings. In particular, you can check a box (which is off by default) that will go a step further and block all unencrypted traffic to a site (Figure 2). You also can set preferences that apply only to particular sites.
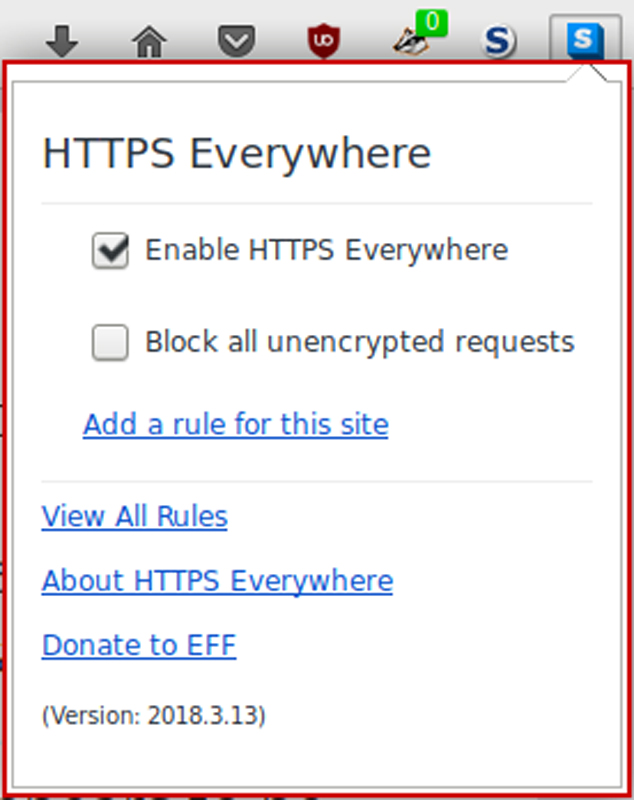
Figure 2. HTTPS Everywhere Settings
I used the AdBlock Plus plugin for many years to block ads on sites. I didn't use it only to block ads themselves but also for my personal privacy and security because along with the ads are privacy-defeating tracking and often malicious JavaScript as well. Advertisers were strongly opposed to ad blocking as you might imagine and in particular focused their attention on AdBlock Plus due to its popularity. Eventually AdBlock Plus announced a program where it would default to allowing certain approved ad networks through. For me, that defeated the whole purpose, so I looked for an alternative and uBlock Origin seemed to fit the bill.
The uBlock Origin plugin works much like AdBlock Plus. Once you install the plugin, it detects and blocks ads from appearing on sites you visit. If you click its icon, it also will show you what it's blocked on the current page and let you allow ads through temporarily just for the current page or for the site overall. It's simple, works well and doesn't require much intervention, so it's become my preferred ad blocker for Firefox.
All of the previously mentioned plugins are things I'd recommend just about anyone use to increase their privacy. This last plugin is a bit different though. I'm old enough to remember when JavaScript was considered a bad thing, and many users disabled it entirely on their browsers (and actually still were able to browse the web). These days, you can't get away with disabling JavaScript entirely—almost all of the web will break. That said, one of the biggest threats to both privacy and security is via third-party JavaScript, so if you want your web browsing to be very secure, you have to figure out a way to block all but the most essential JavaScript from loading.
NoScript is a plugin that lets you select, site-by-site, which JavaScript to run when you load a page. By default, NoScript blocks all JavaScript. When you visit a page that provides JavaScript, NoScript's icon changes to a red circle with a slash through it, and when you click the icon, it shows you the URLs for different JavaScript it has blocked. You then can decide on a per-domain basis which JavaScript to load either temporarily or permanently (Figure 3). Once you make your selections, the page will reload, and hopefully, you'll see more of the site.
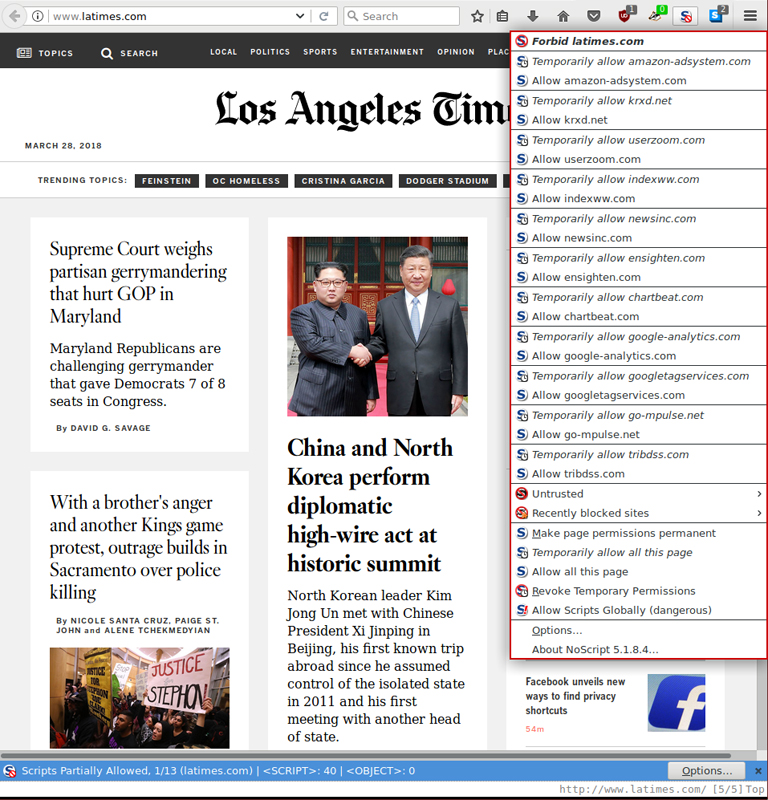
Figure 3. NoScript Output on the Los Angeles Times Website
When you use NoScript, the web becomes very interesting, because at first, a site might have only JavaScript from itself for you to load. Once you allow that and refresh, you might notice a huge number of new sites from all over the web that the first JavaScript now wants to load. It's because of this that using NoScript sometimes can be annoying. Often to get a site to load, you have to become a web detective and track down which of those third-party sites are necessary to load (such as cloudfront.net AWS content or cloudflare.com CDN content) and which sites are loading ads (their domains often contain words like "metrics" or "monitor" in them). It's this detective work that ends up being draining, and you become tempted just to allow all the JavaScript on a site (for which NoScript provides via a handy button).
Because of all of the extra work NoScript requires to work well, and how frustrating it can be sometimes to load new JavaScript continually, only to have yet more to load before a site will work, I don't recommend every user install and use NoScript. For users like me who are particularly concerned about security and want more control over JavaScript though, it's invaluable.
Although many different privacy plugins exist, these four are the ones I use on a daily basis and install across my machines. I hope you find them useful too. These privacy plugins not only protect your privacy, they also can help protect you against malicious sites, and by blocking sluggish third-party sites from loading, they also often can make sites load much faster.