|  |
14.12. Layer 2 Transport Protocol (L2TP)
The Layer 2 Transport Protocol (L2TP) is another generic encapsulation protocol designed to allow you to tunnel IP networking. Like PPTP, it is an extension of PPP. There are two main differences between PPTP and L2TP. First, PPTP always runs on top of IP; it requires that you have an IP connection of some sort. L2TP can run over a number of different protocols, including directly over a phone line (like PPP). Second, PPTP is an encrypted protocol; it encrypts everything except for the initial negotiations. L2TP is not an encrypted protocol; it does not encrypt message bodies. On the other hand, L2TP does do mutual authentication for the initial negotiations and is capable of concealing the information in the initial negotiations.L2TP is normally used in conjunction with IPsec, so that IPsec can provide the encryption. This results in a heavily layered protocol stack. Figure 14-4 shows the layers of encapsulation involved in sending a TCP packet via LT2P securely over an IP network.
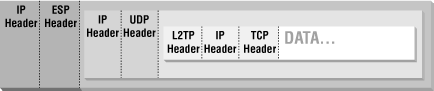
Figure 14-4. L2TP encapsulation of a TCP packet, as normally seen crossing an IP network
14.12.1. Packet Filtering Characteristics of L2TP
When L2TP is layered on top of IP, it uses UDP port 1701. However, in most implementations, L2TP is actually transmitted over IP via IPsec, using ESP encapsulation of UDP; this will have the packet filtering characteristics shown earlier for ESP.| Direction | Source Addr. | Dest. Addr. | Protocol | Source Port | Dest. Port | Notes |
|---|---|---|---|---|---|---|
| In | Ext | Int | UDP | >1023 | 1701 | External client to internal server |
| Out | Int | Ext | UDP |
1701[40]
|
>1023 | Response, internal server to external client |
| Out | Int | Ext | UDP | >1023 | 1701 | Internal client to external server |
| In | Ext | Int | UDP | 1701 | >1023 | Response, external server to internal client |
[40]The standard does not require L2TP servers to return packets from port 1701; they must receive packets at 1701 but may send them from any port. Many servers will send packets from 1701 to simplify interactions with network address translation and dynamic packet filtering.
14.12.2. Proxying Characteristics of L2TP
It is possible to proxy L2TP, as long as you have a proxy system that supports UDP. It's not clear that there's any point in proxying a tunneling protocol, however. If L2TP is unencrypted, it's insecure regardless of what the proxy does; if it's encrypted, the proxy can't tell what it's doing to apply extra security.
14.12.3. Network Address Translation Characteristics of L2TP
In general, network address translation won't interfere with L2TP; although there are embedded addresses, they're intended to pass through a tunnel in any case. Network address translation will not conceal any information when used with L2TP and will not allow you to use L2TP between two networks that are using the same address space, because the original address information will be visible once the L2TP encapsulation is removed.If you use an L2TP implementation where the endpoint sends replies from a randomly chosen port, rather than from port 1701, you may have difficulty getting the replies through an address translation system. The translation system will not recognize the packets as replies because the new source port is not the same as the previous destination port.
14.12.4. Summary of Recommendations for L2TP
- Do not use unencrypted L2TP through a firewall; if you need to cross an unsecured network, be sure that L2TP is combined with an encryption transport protocol. Most implementations will use IPsec for this purpose.
- Proxying does not give you any more functionality than packet filtering when used with L2TP.